0. Foreword:
ADSL technology (asymmetric digital subscriber line) has finally reached the most remote corners of Russia and continues to spread rapidly. More and more users connect to the Internet through an ADSL modem. I will not go into details and describe the work of this technology, I will say in my own words: DSL allows you to transfer data over ordinary two telephone wires with much faster speed than a normal DIAL-UP modem (which transmits data in the audio range - for sure everyone heard the sound of a conventional modem At his work). So DSL (digital subscriber line) is a technology that allows to transmit a signal at higher frequencies (therefore, the speed is higher) on the same pair of wires as the usual low-frequency signal of the audible range. To separate the high-frequency and low-frequency signals, the final equipment is used at both ends of the line-splitters, then by the user: one signal goes to a regular telephone, the second to the ADSL modem; on the second side also one signal goes to the telephone network (ATS) to the second provider. In general, who is not familiar with ADSL, I recommend reading the theory http://en.wikipedia.org/wiki/ADSL
Our subject of close attention is the ADSL modem. Why ask him? Well, in the first, as a rule NAT is embedded in it, the firewall and modem itself is already a serious obstacle in the way of the hacker to the victim's computer. For example, you mailed a trojan or try to get the shell on the victim's computer with 0day-flattening for IE and you do not get anything, because the victim is behind NAT and / or Faer. A home network with a general connection to the Internet, because in the home lokalke as a rule all the balls in free access and having captured one machine on the network you will easily get access to the rest.
Here we will consider the breaking of ADSL modems with Ethernet connection to the user's computer (there is also USB - we do not consider it here).
Like any device connected to the Internet, the ADSL modem has its own IP (it is called external IP, WAN-IP or real IP - as anyone else), as well as an internal IP (LAN-IP) for your lokalka (a gateway to the Internet in Properties of the TCP / IP protocol on your computer).
Between these two interfaces WAN and LAN, and everything else is located (NAT, router, firewall). Remote control of ADSL settings (ie NAT, router, firewall) of the modem is available through different protocols (http, ftp, telnet, etc.). Now the most interesting, by default this remote control of many modems is available both from local and external networks. That is, in other words, the ADSL modem shines with its services both outwardly on the Internet and in the local area network. Many users (= lamers) do not really bother setting up the ADSL modem to ensure their security and leave in the configuration permission to control the modem from outside, ie from the Internet, in addition, even forget (or just do not know) change the password to enter In the configurator ADSL-modem and leave it also default (by default)!
1. Preparation.
A) we need any network scanner (to find the modem configurator built into the ADSL modem of WEB-servers, for example I use LanScope for these cases-it does not contain anything superfluous-it is a multi-threaded network scanner, monitors the network for available resources of NetBios (Samba) , FTP and HTTP, scanning the specified ranges of IP addresses.It shows the access rights to resources: reading, writing.The resource scanner searches for a given resource name, for example, music, video, etc. You can download here the scanner LanScope >
B) minimum knowledge of html and javascript.
C) straight arms and a light head.
2. Search for potential victims.
We scan the plug-in for the presence of ADSL modems. How to find the provider's subnet - easily see your external IP and choose the same or similar range, for example our WAN IP xxx.xxx.241.20 we set the range xxx.xxx.241.1-xxx.xxx.243.255. After a while in the scanner window we will see the services web, ftp, balls. We are interested in web-configurators of ADSL-modems.
3. Actually hacking itself
We start poking the browser into each one, we come to the authorization page of the configurator login (there you will see a banner with a short info such as ADSL modem such and such), enter the password to login. We try the default password 1234, once the modem, two modems, the OPS on the third modem came up (one lame).
(Note how to break the password to enter the configurator read in the following articles, here it is not considered yet)
My victim was http: //ххх.ххх.241.59: 80
Here is the banner and the login page of the ADSL Modem Configurator Web Service
We drive 1234 into the password field and get here:
Then they tell us that the pass is on the silence of 1234 and we should change it (well, we will not change yet, and then the lamak will then have to dump the modem and fiddling with its setting), by this click the ignore button and get here:
We climb into the Wizard Setup Wizard
The login is already visible, the pass is hidden behind the asterisks
This is the html-code of this page.
<html><head>
<meta http-equiv='content-type' content='text/html;charset=iso-8859-1'>
<title>Web Configurator</title>
<SCRIPT src="General.js"></SCRIPT>
<frameset cols="150,*" rows="*" frameborder="NO" border="0" bordercolor="#000000">
<frame src="Panel.html" name="panel" scrolling="NO" noresize frameborder="NO" bordercolor="#000000" marginwidth="0" marginheight="0">
<frameset cols="*" rows="78,*" frameborder="NO" border="0" bordercolor="#000000">
<frame src="Title.html" name="title" scrolling="NO" noresize frameborder="NO" marginwidth="0" marginheight="0">
<frame src="FirstPage.html" name="main" scrolling="AUTO" noresize frameborder="NO" marginwidth="0" marginheight="0">
</frameset></frameset><noframes>
<body>
</body></noframes>
</html>
We see little interesting and that the page consists of frames. We look at frames, for example this FirstPage.html,
We get again on the first page,
But already on a specific file FirstPage.html, we click again on the Wizard Setup, the line in the browser has the form http: //ххх.ххх.241.59: 80 / wzOthers.html,
Click next - now in the browser line http: //xxx.xxx.241.59: 80 / wzPPPOE.html,
Look at its source, here it is:
<html><head>
<meta http-equiv='content-type' content='text/html;charset=iso-8859-1'>
<title>Web Configurator</title>
<SCRIPT src="General.js"></SCRIPT>
<script language="JavaScript">
<!--
function doPPPoEIPAddr(form)
{
if ( form.radiobutton4[0].checked )
{
form.wzPPPOE_StaticIP.disabled = true;
}
else
{
form.wzPPPOE_StaticIP.disabled = false;
}
}
function PPPoEChkIdleTime(form)
{
if ( form.PPPoE_PPPoEVCKA[0].checked )
{
form.PPPoE_PPPoEVCIdleTime.disabled = false;
}
else
{
form.PPPoE_PPPoEVCIdleTime.disabled = true;
}
}
function PPPoEAOLWordChk(Word)
{
}
// -->
</script></head><body bgcolor="#ffffff" marginwidth="0" marginheight="0" >
<FORM METHOD="POST" ACTION="/Forms/wzPPPOE_1" name="ISPform">
<table width="100%" border="0" cellspacing="0" cellpadding="0" >
<tr>
<td width="2%"> </td><td width="5%"></td><td width="93%">
<div align=left valign=top>
<table border="0" cellspacing="0" cellpadding="0" width="560">
<tr>
<td colspan="4" class="NaviText">
<div align=left> Wizard Setup - ISP Parameters for Internet Access</div></td></tr>
<tr>
<td colspan="4">
<hr class="hrColor">
</td></tr> <tr>
<td colspan="2"> Service Name </td><td colspan="2">
<INPUT TYPE="TEXT" NAME="wzPPPOE_ServiceName" SIZE="30" MAXLENGTH="31" VALUE=""></td></tr> <tr>
<td colspan="2"> User Name </td><td colspan="2"> <INPUT TYPE="TEXT" NAME="wzPPPOE_UserName" SIZE="30" MAXLENGTH="70" VALUE="ll2498" onkeypress="chk_chtNumUserName(event)"></td></tr><tr>
<td colspan="2"> Password </td><td colspan="2">
<INPUT TYPE="PASSWORD" NAME="wzPPPOE_Password" SIZE="30" MAXLENGTH="70" VALUE="bukzajop" onBlur="PPPoEAOLWordChk(this.value)"></td></tr><tr>
<td colspan="4"> </td></tr> <tr>
<td colspan="4" class="header2"> IP Address </td></tr><tr>
<td colspan="2"> </td><td colspan="2"> <INPUT TYPE="RADIO" NAME="radiobutton4" VALUE="wzPPPOE_DynIP" CHECKED onClick="doPPPoEIPAddr(this.form);">Obtain an IP Address Automatically </td></tr><tr>
<td colspan="2"> </td><td colspan="2"> <INPUT TYPE="RADIO" NAME="radiobutton4" VALUE="wzPPPOE_RadioStaticIP" onClick="doPPPoEIPAddr(this.form);">Static IP Address </td></tr><tr>
<td width="32"></td><td width="115"> </td><td width="24">
</td><td width="479">
<INPUT TYPE="TEXT" NAME="wzPPPOE_StaticIP" SIZE="15" MAXLENGTH="15" VALUE="0.0.0.0" onBlur="checkIPFormat(this)"></td></tr> <tr>
<td colspan="4"></td></tr>
<tr>
<td colspan=4 class="header2">Connection</td></tr> <tr>
<td width="33"></td><td width="119"> </td><td colspan="2">
<INPUT TYPE="RADIO" NAME="PPPoE_PPPoEVCKA" VALUE="0" onClick="PPPoEChkIdleTime(this.form);"> Connect on Demand: Max Idle Timeout <INPUT TYPE="TEXT" NAME="PPPoE_PPPoEVCIdleTime" SIZE="5" MAXLENGTH="5" VALUE="0" onkeypress="chk_num(event)">sec</td></tr>
<tr>
<td width="33"></td><td width="119"> </td><td colspan="2"> <INPUT TYPE="RADIO" NAME="PPPoE_PPPoEVCKA" VALUE="1" CHECKED onClick="PPPoEChkIdleTime(this.form);"> Nailed-Up Connection</td></tr> <tr>
<td colspan=4 class="header2"> </td></tr><tr>
<td colspan=4 class="header2">Network Address Translation</td></tr><tr>
<td colspan="2"></td><td colspan="2"> <SELECT NAME="wzPPPOE_NAT" SIZE="1"><OPTION VALUE=00000000>None
<OPTION VALUE=01000000 SELECTED>SUA Only
<OPTION VALUE=02000000>Full Feature
</SELECT></td></tr> <tr>
<td colspan="4"> </td></tr>
<tr align=center valign=middle>
<td colspan="6" height="36">
<hr class="hrColor">
</td></tr> <tr>
<td colspan="4">
<div align=center> <INPUT TYPE="SUBMIT" NAME="wzPPPOEBack" VALUE="Back"> <INPUT TYPE="SUBMIT" NAME="wzPPPOENext" VALUE="Next"></div></td></tr>
<tr>
<td colspan="6" height="10"> </td></tr> </table></td></tr></table></form><script language="JavaScript">
<!--
doPPPoEIPAddr(document.forms[0]);
PPPoEChkIdleTime(document.forms[0]);
// -->
</script>
</body></html> Here is the line where our password sits:
<INPUT TYPE="PASSWORD" NAME="wzPPPOE_Password" SIZE="30" MAXLENGTH="70" VALUE="bukzajop" onBlur="PPPoEAOLWordChk(this.value)"></td></tr><tr>
Here is a screenshot:
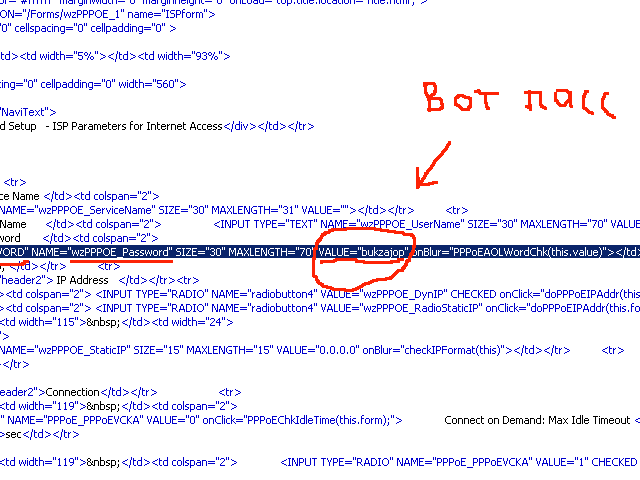
It's easy to guess that the pass is: "bukzajop" , well, and no one hides the login from you in the configurator.
4. Conclusion
Well, what can I say, except as there are llamaks, were and will be, and also holes in the security settings of ADSL modems too. Haha to close the pass from yuzvere asterisks, if it is still mona get it by looking at the html code of the desired page. Well, I do not need to explain how to set up an ADSL modem, for example, you can make a forwarding of packets (NAT settings) on all protocols and ports from an external IP to an internal one and break (explore for bugs) services on a computer on a local network, and You can take and switch the modem to bridge mode, thereby making the modem transparent and transfer the external IP to the computer and then scan its computer with security scanners for holes in the network services.




Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.