Hacking and protection of WebMoney
Contrary to all the assurances of developers, the WebMoney system is catastrophically unreliable and is opened literally with a fingernail. There are many worms, Trojans and hacker groups that specialize in the theft of electronic wallets, theft of which took a massive nature. Do you want to know how this is done and how to protect yourself?
Introduction
Let's start with something that can not be. No "WebMoney generators" exist and can not exist in principle. All the cash is stored on the central server of the operator, and electronic wallets are only a means of access to it. Roughly speaking, from the fact that you will generate a combination of digits for the code lock, money and jewelry in the safe will not appear. And although there is an opportunity to choose a cipher to someone else's safe, the probability to open it without the help of the owner (we remember about the soldering iron, but we are silent) is so small that it is not even worth talking about!
But steal someone else's combination is real! This is what "WebMoney generators" are doing. They either make a duplicate from the electronic wallet and transfer them to the attacker, or they secretly call Keeper and transfer to their account. Similarly, there are viruses and Trojans. Also marked and targeted attacks on a particular victim. Can I protect myself from them? The WebMoney system, developed by non-specialists, was originally designed without regard for security and, although recently a whole complex of "fire-fighting" measures prilapannyh hindsight, the situation remains critical. Users are confused in security systems, the support service gives rather vague and vague recommendations (update Windows, configure the firewall, etc.), and meanwhile the theft of electronic wallets continues.
We do not set ourselves the task of teaching anyone how to steal, we just want to show and prove (!) That the WebMoney system is really very unreliable and was projected not even by an ass (it nevertheless is adjoined by the spinal cord), and in general it is not known what . There will be no vague words (so that we are not accused of libel), but there will be no concrete recommendations. We do not give ready attacking programs and do not say which baitics you need to hack, but believe me - all the necessary hacking tools can be created from scratch in one night - a sacred time for hackers!
But first things first. We will not rush ahead and poke the laser disk into the drive, especially since the latter will still be needed.

Figure 1. They appear from the darkness, take off all electronic money and go nowhere.
WHAT IS POSSIBLE AND WHAT CAN NOT (REVENUE)
Experimenting (for educational purposes) is possible only with its own electronic purse or with the purses of persons who have given written permission. Unauthorized interference with other people's systems and wallets is absolutely unacceptable !

Figure 2. They catch those who come from the darkness, and are taken to the world from which there is no return.
Beginning began or classic missionary
The WebMoney system is a kind of analogue of ordinary bank checks, which means that to make payments, we must first register on the central server of the operator and open an account, which is already a huge drawback, well, okay.
We go to www.webmoney.ru , download the Keeper Classic program, run it (by the way, make it work through the Proxy server, this miracle of scientific and engineering thought I did not succeed, I had to lift NAT and mapp 2802 port), fill out the registration data (from Lantern or honest), we come up with any password for our taste, after which the program proceeds to generate a secret key and asks us to tug the mouse and press the keys. This is necessary in order to get really random data, as if the timer-based pseudo-random generator is not suitable here. Against the background of the general insecurity of the system, brave with the words RSA, RC5, MD4, MD5, SSL is just silly. However, the psychological calculation of the developers is understandable to me. If the secret key is generated in a fraction of a second - which user will believe in it?

Figure 3. It does not appear anywhere, does not catch anyone, but simply sits and solder.
Whatever it was, upon completion of registration, we are assigned a unique 12-digit WMID (Web Money ID) ID, and a key pair is generated. The public key is transferred to the central server of the WebMoney operator, and the secret key is stored in a file with the extension * .kwm (Key of Web Money), which can be located on the hard disk, removable media or smart card. In short, ordinary asymmetric cryptography such as PGP.
Another file is created * .pwm, which stores information about our wallets (current balance, transaction history, etc.). In principle, it is not necessary, because all information is located on the central server of the operator. Keeper can work without a * .pwm file, automatically uploading data from the network, though only for the last three days. In fact, * .kwm file is also optional and can be restored. To do this, you need to know the password, have access to the mailbox specified at the time of registration, as well as a notarized statement that you are not moose (more about this you can read here: http://www.owebmoney.ru/returnkey.shtml ). Theoretically, a hacker can hack our money only on the basis of a password, but in practice this is too troublesome and unsafe.
Secret information, regulating access to the wallet, is only a kwm-key. WMID is published everywhere openly and this is normal. Knowing WMID, you can find out the user's login information, which he marked "open", but you can not determine the number of his wallet (purses).
The purse number is a conditionally confidential information. Knowing the purse number, we can not withdraw money from it, but we can issue an invoice by filling out the "description of the purchase" field as plausibly as possible. The way of course, stupid, but there is some chance that it will pass. Users regularly paying a large number of small accounts are gradually getting used to not paying attention to them and checking the column "from whom" only if there are doubts. Of course, there is no buzz in this way of hacking, besides, an intruder can very badly burn and go to the company of an uncle who will tear his ass, so that he has not found any appreciable popularity.
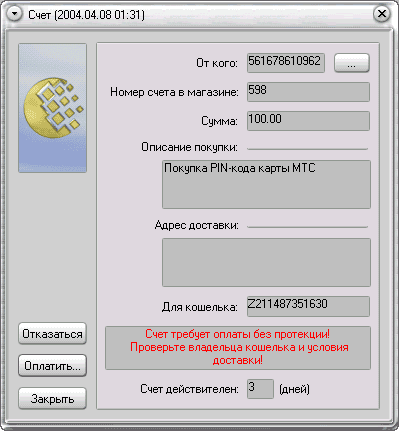
Figure 4. We expose the victim to the left, but believable account - suddenly and pay?
But stealing kwm-files is thriving. By default, the keys are stored in keys.kwm, but, in principle, the file name can be anything, as, indeed, the extension. Most hackers and Trojans make a dumb search for the * .kwm mask, so renaming the key file in dontreadme.txt somewhat increases our security, however advanced hackers can get into the registry where Keeper stores its settings and peeps the path to the file. You can also search by its contents, scanning all files (though it will take a lot of time and cause suspicious disk activity). Gourmets will probably intercept the call to the CreateFile API, which shows which files Keeper opens. And even if the format of the registry settings in subsequent versions is changed, the option with CreateFile will continue to work (hint: if the developers were not idiots, they would create several files with the keys - one authentic, all the others - watchdog sensors, Anxiety).
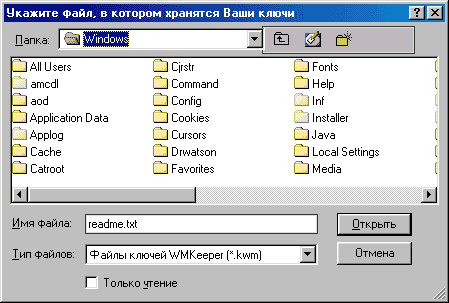
Figure 5. Hide the kwm-file away from hackers.
By default, the size of the key file is 1.2 MB (in exact order, on a floppy disk), but you can increase it to 100 MB if desired. This makes it difficult to steal the key with the transmission over the Internet, and, in general, does not create any insurmountable inconveniences. 100 MB is half a mini CD-R, one Zip-100M or two CD-Rs in the format of a business card. Of course, the system's performance will fall to some extent (a huge file does not immediately read), but security is worth it. Or is it not worth it? On the local network to drag 100 MB is not a problem, by DSL modem or cable Internet - too. And even a shameful by today's standards modem at 33600 will give this file for ~ 70 hours. Not so much, if you remember that virtually no user will regenerate the keys every day. Cutting the file into small pieces transmitted in the background, dragging it in two or three weeks is quite possible, although it will be the most dull and unpromising way.
If a hacker infiltrates someone else's system (and you can penetrate it in different ways), it's not worth it to download the file into memory, open the wallet, transfer money to your account and bang the hard drive so that the victim can not enter the Internet and complain to who should . By the way, at the expense of "complain." There are not so many options, and there is no way to help. Well, perhaps from the Lord God (if you're real god, return my money, you sic fuck) yes to the brothers. If we still have access to WMID (which is a stupid hacker!), You can determine the WMID to which the money was transferred, go to the Arbitration Service website ( http://arbitrage.webmoney.ru/ ), pay the arbitration fee (a For this it is necessary to have WebMoney, which we have cleaned up by the intruder) and block the hacker wallet. Only if the hacker is not elk, money for a few minutes will be transferred to e-gold or by any other way withdrawn from the system, so that on his purse they will not be and will be blocked especially and there is nothing. By the way, wallets with an initial or personal passport are blocked only by the decision of the arbitration commission, that is, it is enough to take the certificate and ... Just do not say that the owners of the certificates do not steal because they report their passport data. Agashchazblin! Taki your own? The issuance of the certificates are now being taken care of by everyone who is not too lazy and hoping that they are all honest, conscientious and incorruptible people, just naive, especially when it comes to money, even electronic money. A man who intended to steal $ 100,000 (and why not), will get no problems not only a fig certificate, but also a false passport in return. Well, who on this certificate then look for? Even if employees of the Ministry of Internal Affairs forge passports on the stream, which TV often spoke about (which is criminal), then what about "certificates" that do not have any legal status at all?
However, the situation with the transfer of stolen money through several purses still considered developers, and they carefully enslaved the ... intruders! Judge for yourself. The victim after submitting the already mentioned claim should contact the Administrator of the Arbitration Service (WMID 937717494180, [email protected]), and ask him to follow the whole chain. All the "charm" is that the Administrator works only from Monday to Friday from 10 to 18 hours in Moscow. We, they say, are not a rescue service and we also want to sleep. Very good payment system, I tell you! With the fact that the withdrawal of money from the system is almost instantaneous and the account goes on for minutes, the administrator, you see, wants bainki. I do not understand, is it a student hostel or a payment system ?! What was worth while at millions of revolutions (of which advertising does not cease to mention) to hire several people for round-the-clock support? After all, it is about money in this case! Naturally, it's safer for hackers to commit theft either at midnight or on weekends. But it's okay, leave empty words and get acquainted with Keeper'om closer.
Keeper outside and inside
Here, some people admire how the developer managed to squeeze so much into the volume of Keeper (" I do not know about you, but I sincerely admire those who, in 2 megabytes of the Keeper Classic distribution, managed to invest such a" tasty "stuffing, and even beautifully pack it This is the case from the outside ", http://www.owebmoney.ru/clashistory.shtml ). And what, in fact, did they contain in it? Of course, in this age, when "Hello, World!" With difficulty will interfere with the laser disk, programs that occupy "just" a few megabytes already cause respect ...
The main volume (~ 2.2 MB) is occupied by WMClient.dll which, in fact, Keeper itself is. This is a DCOM object written in Microsoft Visual .NET with compilation into machine code, not packed and nothing, I repeat, does not interfere with its analysis. There is no encrypted, no p-code, no anti-debugging techniques, no resistance to a disassembler, a dumper, an API spy. Nothing! Take-and-analyze! In any case, version 2.4.0.3 (the latest at the time of this writing) behaves exactly like that. If developers are a bit smarter, they would either use Microsoft Visual C ++ 6 (the famous "six") plus any high-quality protector (for example, ExeCryptor), or compile the NET-application into p-code, which is much more difficult to disassemble.
WebMoney.exe (~ 180 Kbytes) is just a "puskalka" and there is nothing interesting in it, nevertheless it still costs to disassemble it. At least later, to laugh at the developers and assess their qualifications.
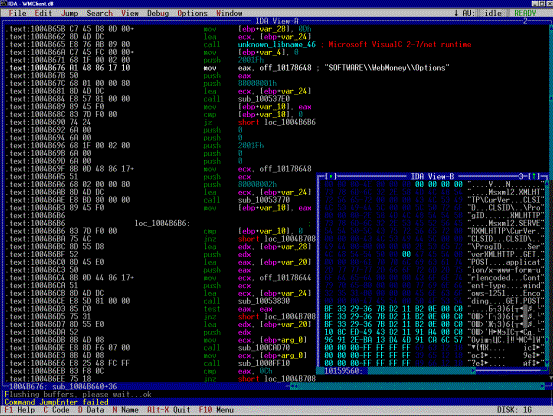
Figure 6. Keeper Classic in the disassembler.
So, let's assume that a computer with Keeper installed is embedded with a hacker code that executes with user privileges (let's agree that we have not been given administrator rights and, although to increase our privileges from the user to the system in W2K / XP, in general, Not a problem, let alone 9x, where there was no division of privileges, we will act in Spartan conditions, close to the combat ones). What we can do? We have two ways. Pre-disassemble Keeper'a, restore the protocol of exchange with the server, wait for the media to be inserted, which is the secret key and ... then fantasize yourself. Personally, I poke around in Keeper'e laziness. Disassembling is a painstaking business and it may take several weeks to restore the protocol of exchange. The use of sniffers significantly shortens this time, but still "vlom". It is much easier and more effective to steal money with the help of Keeper himself. We install a spy intercepting the keyboard input, wait for WMID input or define it in other ways, because WMID is not a secret to anyone (the first method is mainly used by viruses, the second method is good for targeted attack), then one "perfect" moment After 18 hours or on the day off) we disable the output to the screen, launches WebMoney.exe and by emulating the keyboard-mouse input, everything we wanted. For example, we replenish the purse of the victim. Why not?! We're breaking our own wallet, right? That's it and replenish it! We are not gangsters, but honest hackers!
The technique of input emulation is described in detail in "Notes of myshh'a", the electronic version of which can be chewed free of charge from my myshkh'inogo ftp-server ftp://nezumi.org.ru/ (only to remind that it is not available all the time), to In addition, in the 67th issue of Hacker, an article "WebMoney" was published in which all this is described. So we will not breed demagoguery and chew rubber a hundred times. We note only the general mechanism. First we find the Keeper window by calling FindWindow or EnumWindows and defining its handle. Then, using EnumWindows, enumerate the child windows belonging to the controls (buttons, edit lines, etc.). Sending various messages to control elements (this can be done with the SendMessage function), we easily take them under our control. Disabling the output to the screen is performed either by intercepting GDI services (implemented in a complicated way, but acting on hurray) or by placing a distracting window on top of the Keeper, for example, a browser window with a pornographic image. Yes, many things can be invented here!
The problem is that, from some time on, dull emulation has ceased to function. Keeper got the so-called "flying figures". Like those used to prevent automatic registration on many sites. Before making any payment, you must enter three graphic numbers, which randomly appear on the screen. The idea, of course, is interesting, but here it is borrowed obviously out of place. Heavy childhood, shitty education, deep hangover. And your head is bo-bo. However, the head here not and. All the same, she has no one to think. Developers obviously did not learn security techniques. Sketchy knowledge in the style of "here crammed, and then the girl danced, and then I moved a brick" and a rod from all sides.
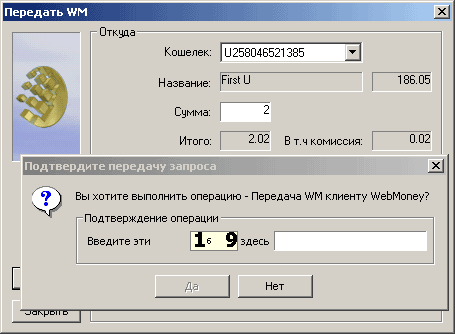
Figure 7. Protection Keeper'a "flying figures."
Why do "flying numbers" act on Web servers (where they first appeared)? Because , firstly, the security code is beyond the reach of the hacker, and, secondly, because the protection is aimed solely at robots, but not people. To protect mail.ru from spammers and vandals, this measure is more than enough, but not for Keeper! Firstly, in current versions of Keeper, flying figures are elementaryly recognized by simple OCR, which can easily fit into a hundred kilobytes (using ready-made libraries); secondly, hacker code does not cost anything to grab a piece of the screen and send it to a monitor hacking at the monitor to He recognized them himself, thirdly, this protection is turned off bit-hack, i.e. Editing of Keeper's machine code; fourth, flying numbers can be cut through the registry (if you try to disconnect them by Keeper's means, he will ask for confirmation of the legitimacy of this operation); fifth, even if the protection is toughened, in reserve Hackers will remain the decryption of the protocol of exchange and the creation of their own customers without any figures there, in the sixth ... In short, the methods of hacking are very, very much and there is no benefit from this protection, not to mention that many users are still sitting on Old versions without flying numbers or turn them off as unnecessary.
And here is another widely advertised chip - confirmation of authorization by e-mail. At an inexperienced look, everything looks iron - before we manage to do anything with our account, it is necessary to enter the code that will come by e-mail. If the hacker rebukes the * .kwm file, it will remain with the nose, and we - with the money. After all, he will not get access to our mailbox. Logic is iron, but wrong. Mailboxes are not so difficult to break (specific methods of hacking are listed in many books and articles, so I will not repeat it), besides, as soon as a hacker has dragged a * .kwm file, he will also drag the password to e-mail. The exception is, perhaps, only the theft of smart cards and removable media with keys, but ... such theft, as a rule, is carried out either by close people who can have e-mail or robbers who have got physical access to the removable media, , Usually in the immediate vicinity of the computer. Well also what it is necessary to them to steal still and the password on a box?
Okay, but what about blocking all IP addresses except your own? To begin with, in local networks, seizing someone else's address is not an insurmountable problem. The same one who is sitting on the Dial-Up will usually receive dynamic IP addresses allocated from the shared pool. Prescribe them - you get bogged down, and any client of the same provider will be authorized without any problems. But it is not important. No hacker to keep someone else's wallet fucking is not necessary. He will simply withdraw money with Keeper's hands, launched on the victim's computer, which probably has the correct IP and no "blocking" it does not stop!
The protective measures proposed by the developers can be listed for a very long time. Almost all of them are focused on theft * .kwm file with the subsequent transfer of it over the network. For some reason, the developers think that this is the only way to hack, although this is far from the case. They also advise to "properly" configure the firewall to prevent information leaks and regularly patch the system so that neither hackers nor worms infiltrate. Well, at the expense of firewalls, they clearly got excited. It is enough to go to the popular site http://www.firewallleaktester.com/ to make sure that there are attacks that pierce all personal firewalls. I also wrote about this in the "Notes of the researcher of computer viruses", fragments of which can be downloaded from ftp://nezumi.org.ru/ , there is also a ready demo code.
Now let's look at the updates. Many sites accepting payment via WebMoney only work with IE, because they use ActiveX. And although plug-ins are released for alternative browsers like Opera and Fox, they work somehow and in reality you have to use IE, the number of holes in which is worthy of the Guinness Book of Records. That is, the creators of WebMoney themselves podsazhivayut us on the holey browser, and still carefully recommend - do not forget to update in time, they say. Maybe I should change sex too ?! So, the problem is not with users. The problem in the brains of the developer (or rather, in their complete absence). The problem is in the concept of the whole system. The problem is the fundamental vulnerability of the protocol of money transfer and Keeper's vulnerability. Hell, how many years already there are algorithms for generating "one-time" keys, in which there is simply nothing to steal and nothing to steal. But why I know about them - quite far from cryptography and financial frauds myshh - but do not know the developers of the payment system? Ponaprimanali it is not clear who ...
Keeper light or the fight against certificates
The insecurity of the classic Keeper is a common fact, but Light is still considered quite secure: " In Keeper Classic, you can drag the file with the keys in parts, email can be hacked, etc. The keys stored on the removable media can be written to the hard drive in the The moment when a floppy disk or CD is inserted in. That is, it is theoretically possible to get to the money, although with all precautions, it is extremely difficult . But Light with a non-exported certificate gives a 100% security guarantee "( http://owebmoney.ru/ Cafe / index.php? Showtopic = 108 ).
It sounds tempting, but how does this work in practice? Let's try to understand. Let's start with the question - how does Keeper Light work? Very simple. The secret key is now stored not in the * .kwm file, but in a special certificate, and all management goes through a Web interface using special cryptographic protocols.
Where does the browser store certificates? Depends on the browser itself. For example, Mozilla - in the directory "./mozilla/defaul/<blahblahblah>/cert8.db", but IE, running under Windows XP Professional, uses a fairly heaped system. Certificates with public keys are stored in a personal (personal) store located in the Documents-n-Settings \ <username> \ Application-Data \ Microsoft \ SystemCertificates \ My \ Certificates directory, which is free for everyone (it's public information!) . User certificates are located in his profile. Closed keys are stored in the Documents-n- Settings \ <username> \ Application Data \ Microsoft \ Crypto \ RSA directory. All files located here are automatically encrypted with a random symmetric key - the user's master key, 64 characters in length. The main key is generated by the Triple DES algorithm based on the user password with which it is logged on.
What does all this theoretical bodyguard mean in practical terms? And the fact that you can not steal a certificate with a private key from under Windows XP! That is, it will be possible to steal something, but it will be no use to it, since it will simply not work on someone else's computer! (On that he and the closed certificate!). True, it can be exported without even having any special privileges. Rip the Certification Manager program if you do not know how. In fact, to transfer certificates from computer to computer, Keeper Light uses the exported certificate, which is stored in files with the extension .pfx. They can be found both on external storage media and on hard disks. Here only there is one "but". The exported certificate is closed with a password assigned by the user, and to import it into your system, you must either throw a keylogger or try to open the password by brute force. But the first is too noticeable, the second is long, so theft of certificates has not been widely spread.
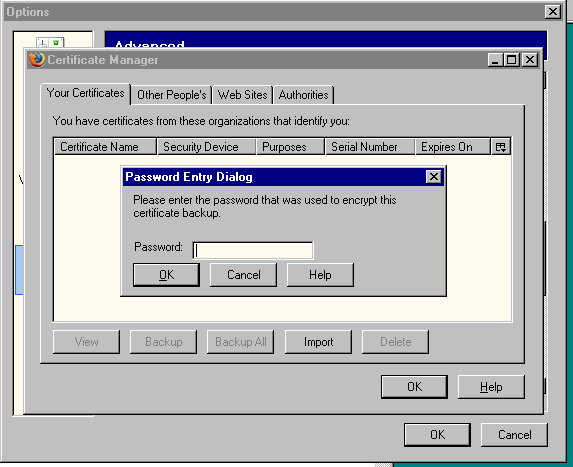
Figure 8. Requesting a password when importing the certificate.
Does this mean that Keeper Light is protected? No and no again!!! If Keeper Classic can be protected at least theoretically (install a driver that provides direct keyboard input, cuts emulators and monitors Keeper's integrity and itself), then Keeper Light works through a browser whose "integrity" can not be controlled in principle!
The first thing that comes to mind is the already mentioned emulation. We say "start https://light.webmoney.ru", hiding the browser window in one way or another (just get its handle and draw on top of it, which is horrible) and emulate the keystroke sequence to replenish the electronic wallet. Acts ironically and inevitably. The only downside - each type (and, possibly, the version) of the browser requires its approach, but you can only focus on IE 5/6, as the most popular one.
The rest of browsers are even easier. We take the source of the Fox and create a hacker mini-browser based on them, which does not display anything on the screen, but it only works with wallets. True, among fans of WebMoney, Fox fans are not so many, but it's still better than nothing at all. By the way, let the adherents of IE do not feel safe. The source code for W2K was stolen a long time ago and it's quite possible to create your IE clone on their basis, not to mention that IE is just a collection of DCOM objects and even a beginner can build a browser based on them.
Figure 9. Keeper Light - it's just a WEB-interface, which allows you to work with your wallet through any browser.
And what if you import the certificate before each opening of the wallet, and then delete it from the repository? Indeed, this will increase security to some extent, however, a hacker program can either wait for the "WebMoney Keeper :: Light Edition" window to appear, signaling that the user has logged in, or spying on keys, passing a secret password along with the certificate over the network. So, electronic money is still in a delicate situation!
Authorization by cell phone - reliable?
The last squeak of the fashion was the system of authorization with the help of a cell phone. When registering with the ENUM service ( http://enum.ru/ ), a special Java application (also called a MIDlet), which calls itself the Enum Client, is installed on the mobile phone. It takes five-digit numbers (for example, 09652) and generates a response based on them, and the generation algorithm is unique for each user. If there is no cell phone - Pocket PC or any other device with Java support (for example, a desktop PC, will only make sense in it).
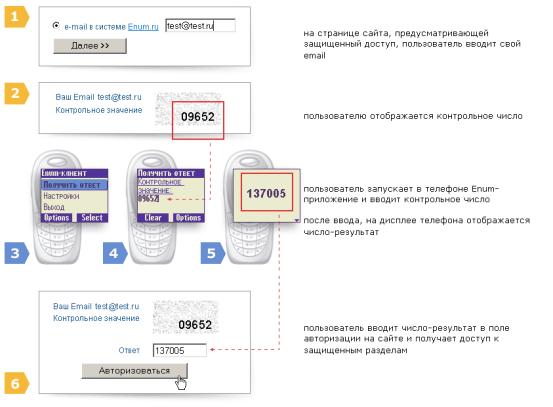
Figure 10. Sequence of operations when the payment is activated via a cell phone or PDA.
ENUM service allows you to make purchases through the Merchant service ( https://merchant.webmoney.ru/ ) without resorting to Keeper at all - neither to classical, nor to the cloned. It is believed that to crack an electronic wallet and steal cash in this case will not be possible: " Scammers and virus writers use the Internet to steal valuable information from our computers, but whatever protection we have invented - firewalls, antiviruses, antikaylogers, antitrays, certificates - there is always The theoretical probability of it being circumvented and stealing passwords (or Keeper's keys, for example) from the computer, because both hackers and defensive tools use ONE SAME channel - the Internet.And the Internet problem is that there is no other, alternative storage-transmission channel ENUM solves this problem, it provides us with that other channel.The hacker can get on your computer, "hook up" the Trojan virus, but it can not fit into your mobile phone .How to guess what unique for each user Algorithm Enum Client from one number gets another, too it is impossible "( http://owebmoney.ru/enum.shtml ).

Figure 11. ENUM system logo.
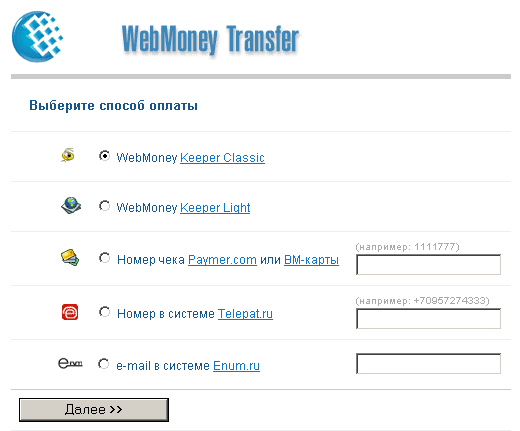
Figure 12. Service Merchant.
Is it true? As the saying goes, "if you can not, but really want, then you can still." An additional "communication channel" indeed increases the security many times, but it is premature to talk about the principle impossibility of hacking. To begin with, the algorithm for generating numbers for all users is still the same (disassemble the MIDlet, if you do not believe it), only the generation key is different and it is quite possible to select it. It is enough to intercept a single response for this combination of numbers. Restoring the key does not take long and the Trojan program is quite capable. I hope you do not need to explain how to read a combination of numbers from the edit box.
In addition, cell phones contain a bunch of holes. IR protocols and Blue Tooth literally swarm with them. The magazine "The Hacker" repeatedly wrote about this. If the victim has a cell phone or PDA, then maybe she has both a Blue Tooth or IR adapter that keeps it on constantly. An attacker can send any AT commands to the phone, execute midlets or read their contents. And what ?! You can poke and write a virus that steals electronic purses and sends them through a cell phone! Bypassing all firewalls! Here's an additional channel for you!
However, all this is a nit-pick of the old myshkhastny hacker. The mood is just bad. It's raining, and only Sirenia saves the depression (a very powerful gothic band from faraway Norway - I recommend). If you soberly look the truth in your eyes (in such red myshh'inye eyes - small, like beads), you must admit that hacking ENUM is very difficult, so that there is some meaning in it. But this does not mean that you can start an electronic wallet and safely put $ 100,000 on it. Then surely they will hack!
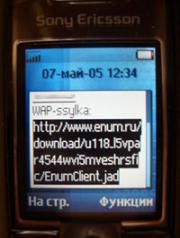
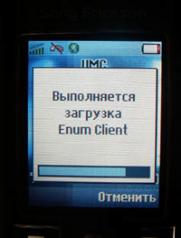
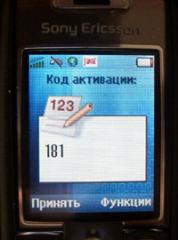
Figure 13. Activation of payment by cellular phone through the ENUM system.
How to break exchangers
The hacking of exchangers is not included in our plans (not everyone owns their own exchanger, and it's illegal to break strangers), therefore, we only note the main points. From a hacker point of view, the exchanger represents a site, usually managed by PHP and running under Linux / BSD / NT.
Here through errors in PHP-scripts they are often broken. Also, some Web programmers leave the back door in case they suddenly want to eat, and there will be nothing to eat. Rarely break the axis. The largest number of holes, of course, is NT and all its derivatives (including the praised Windows 2003 Server). Linux and BSD break a bit more difficult, but ... if you take a security scanner (for example, X-Spider), you can find that many of them are clumsy SendMail or rusted Apache. Buffer overflow, sending shell code and the server in our hands!

Figure 14. The workplace of the hacker.
Conclusion
Hacking WebMoney is not a myth, but a harsh reality and you can not be 100% secure, even if you are a security expert. There is always a risk of catching a virus through an unknown hole in the operating system or browser, and if from the loss of operational data on the hard drive rescues the reservation, from the disclosure of confidential data - the physical disconnection of the Intranet from the Network, then theft of electronic money does not save anything!

Figure 15. Sireina - Gothic hacker music, that kolbasit myshkh'a.


Comments
Commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.