Catch a spy or "Where does the computer mail send ..."
Now it is difficult to find a person who has not heard the word "Trojan", and whether there are not enough other programs that are unnoticeably sent by the user, either about him or about him. Next, I'll write about how to find out to whom and what (for example, your passwords) stealthily send programs such as "Trojan Horse". The principle of the action of these programs is that the attacker gets access to the files and folders of the hard drive, can run various applications on your computer and "take pictures" of the screen. The Trojan consists of two programs: the server and the client. The server is a program that runs on the victim machine and executes the client's commands. A client is at the attacker with the help of which he manages the server. When you get to the computer, the program is written to autorun and invisibly starts with the operating system. Trojan can be downloaded from the Internet with a harmless program. It is glued together. It is very simple to use trojans, we must make the victim run the server of the program (if you are on the local network, you can go and run it yourself  ) Then in the client part enter the ip address of the victim, click connect .....
) Then in the client part enter the ip address of the victim, click connect .....
Protection: Use the latest AVP antiviruses, DrWeb and do not run unknown programs (especially those that came with the mail), as well as progs with the DOS icon (blue square). An effective protection method is the Firewall
How Trojans Send Your Passwords
Like other email programs, Trojans use Simple Mail Transfer Protocol (SMTP) to send messages. In order to send a message, the program connects to the SMTP server and sends it, the most interesting is that you can track the entire process using Sniffer. ( Sniffer is such a program that "catches" the necessary information transmitted both in the network and from a separate machine if it is installed on it, that is, you can monitor what data your computer sends and receives ) I will look at the example of the Network Spy sniffer, in general Any sniffer for Windows will do. First you need to configure Net Spy, so that only the information we need is displayed, and the service type arp, icmp ... of the package was ignored, for this you need to run the program and go to the filter settings: Menu "Options" In it, "Manage rules ... "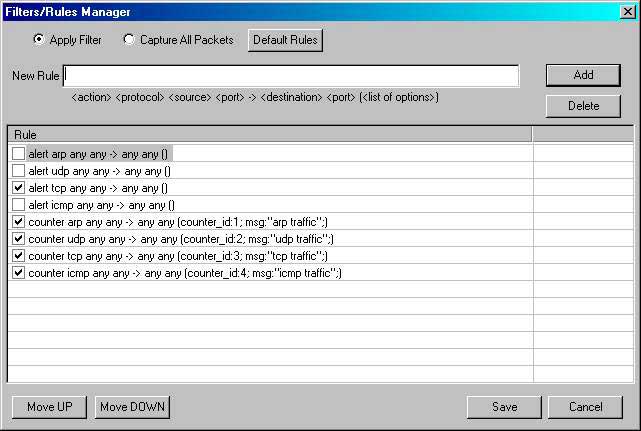
Those. Only TCP will remain.
When will Trojan send passwords? Of course, when connecting with the Internet, it is possible that only when a new connection appears and with it new passwords. So we create one more dalap connection, with the password Anti- 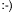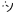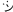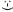 This is what the "hacker" will receive in a letter from his Trojan
This is what the "hacker" will receive in a letter from his Trojan  Open the sniffer and launch it (clicking on the green arrow), connect to the Internet on the old connection, and wait for the Trojan server to start sending our passwords, in about a minute, maybe more you will see something like this:
Open the sniffer and launch it (clicking on the green arrow), connect to the Internet on the old connection, and wait for the Trojan server to start sending our passwords, in about a minute, maybe more you will see something like this:
Those. NetSpy records everything that is passed to the smtp server, and now it is no longer difficult, according to available information, to know who and what was sent  Each line shows one packet: in the first column time is written, in the second IP-address of the computer that sent the packet, in the third-ip-address of the destination. If you go to the "Action" menu and choose "Resolve IP's" there, then the IP-addresses will take the usual form and it becomes clear what smtp-server the program uses to send mail. Then comes the size and at the end indicates the protocol type, we have it smtp ie. Immediately understand that this is sending mail, and if for example POP3, IMAP4, then this is the delivery of letters from the server, well, HTTP is so clear .... Now double-clicking on any line, you can "Decode" this package, Information about it: MAC and IP-addresses from where and where to go, protocol type, TTL, size, etc. And at the bottom of the transmitted information. Select the largest packages and see (you can switch from one to another by using the arrows "forwards", "back" in the opened window with the decoded package) in them you can find the header of the letter with the address of the recipient, as well as the text of the letter.
Each line shows one packet: in the first column time is written, in the second IP-address of the computer that sent the packet, in the third-ip-address of the destination. If you go to the "Action" menu and choose "Resolve IP's" there, then the IP-addresses will take the usual form and it becomes clear what smtp-server the program uses to send mail. Then comes the size and at the end indicates the protocol type, we have it smtp ie. Immediately understand that this is sending mail, and if for example POP3, IMAP4, then this is the delivery of letters from the server, well, HTTP is so clear .... Now double-clicking on any line, you can "Decode" this package, Information about it: MAC and IP-addresses from where and where to go, protocol type, TTL, size, etc. And at the bottom of the transmitted information. Select the largest packages and see (you can switch from one to another by using the arrows "forwards", "back" in the opened window with the decoded package) in them you can find the header of the letter with the address of the recipient, as well as the text of the letter.
How the Trojan is updated
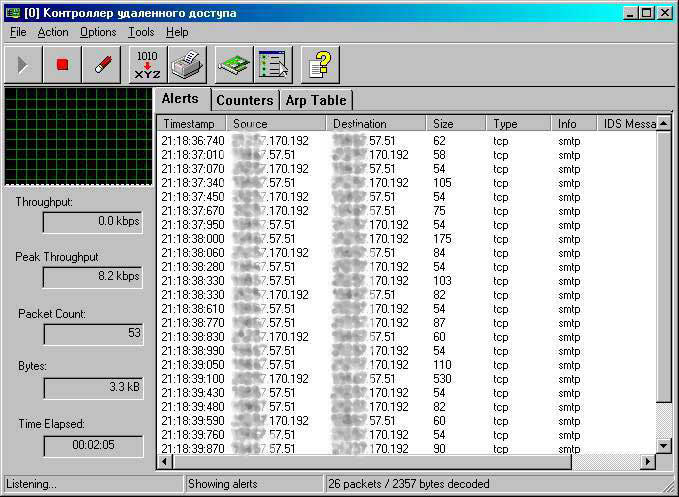
In addition to sending passwords, many Trojans have a "self-updating" function when it downloads a file from the Internet and launches it, if this is so in the sniffer window, there will still be packets transmitted over the http protocol (80th port), As well as in the previous one Case it is necessary to save everything to a file, then again we will use the search in the text, this time we need to search for the word "GET" after it the requested address is specified:




Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.