How to decompile eval (base64_decode ()); Eval (gzinflate (base64_decode ()));

Basic principles of encryption and packaging, weaknesses of protection, ways of manual removal, as well as universal tools for automatic removal of packers and hinged protection from JavaScript scripts.
Recently, more and more often the source code of scripts is encrypted or packaged.
Yandex, DLE and other popular projects began to get carried away, and beautiful bikes about "taking care of users", "saving traffic" and other nonsense look very funny.
Well, if someone has something to hide, then our task is to bring them to clean water.
Theory
Due to the peculiarities of JavaScript execution, all ciphers and packers, in spite of their diversity, have only two variants of the algorithm:
Var encrypted = 'encrypted data';
Function decrypt (str) {
// decryption or unpacking function
}
// Run the decrypted script
Eval (decrypt (encrypted));
Or as an option:
Var encrypted = 'encrypted data';
Function decrypt (str) {
// decryption or unpacking function
}
// Display the decrypted data
Document.write (decrypt (encrypted));
The second method is most often used to protect the original html-code of the page, as well as various Trojans to introduce malicious code into the page, for example, a hidden frame.
Both algorithms can be combined, the "heap" and entanglement of the decryptor can be any, only the principle remains unchanged.
In both cases, it turns out that the eval () and document.write () functions are completely decrypted.
How to intercept them?
Try to replace eval () with alert () , and in the opened MessageBox you will immediately see the decrypted text.
Some browsers allow you to copy text from MessageBoxes, but it's better to use such a semi-automatic decoder:
<Html>
<Head> <title> JavaScript Decoder </ title> </ head>
<Body>
<Script type = "text / javascript">
// The function of writing to the decryption results log
Function decoder (str) {
Document.getElementById ('decoded'). Value + = str + '\ n';
}
</ Script>
<! - Log window ->
<Textarea id = "decoded" style = "width: 900px; height: 500px;"> </ textarea>
<Script type = "text / javascript">
// Insert the encrypted script here, in advance
// replace all eval () and document.write () calls with decoder () in it.
</ Script>
</ Body>
</ Html>
For example, let's take some script from Yandex , after looking at the source code we see something unhealthy:
eval(function(p,a,c,k,e,r){e=function(c){return(c 35?String.fromCharCode(c+29):c.toString(36))};if(! ''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e ){return r[e]}];e=function(){return'\w+'};c=1};while(c--)if(k[c]) p=p.replace(new RegExp('\b'+e(c)+'\b','g'),k[c]);return p}('$.1e .18=8(j){3 k=j["6-9"]||"#6-9";3 l=j["6-L"]||".uL";3 m=j["6-L-17"] ||"";3 n=j["1d"]||0;$(5).2(".6-9").14("7");$(5).2(".6-9").Z("7",8( ){3 a=$(5).x();3 o=$(5).x();3 h=$(5).B("C");$(5).v("g-4");$(5).16( $(k).q());3 t=$(o).2("15");3 c=$(o).2(".br");3 d=$(o).2(".b-12"); [остальной такой же бред отрезан] eval(function(p,a,c,k,e,r){e=function(c){return(c 35?String.fromCharCode(c+29):c.toString(36))};if(! ''.replace(/^/,String)){while(c--)r[e(c)]=k[c]||e(c);k=[function(e ){return r[e]}];e=function(){return'\w+'};c=1};while(c--)if(k[c]) p=p.replace(new RegExp('\b'+e(c)+'\b','g'),k[c]);return p}('$.1e .18=8(j){3 k=j["6-9"]||"#6-9";3 l=j["6-L"]||".uL";3 m=j["6-L-17"] ||"";3 n=j["1d"]||0;$(5).2(".6-9").14("7");$(5).2(".6-9").Z("7",8( ){3 a=$(5).x();3 o=$(5).x();3 h=$(5).B("C");$(5).v("g-4");$(5).16( $(k).q());3 t=$(o).2("15");3 c=$(o).2(".br");3 d=$(o).2(".b-12"); [остальной такой же бред отрезан] At once I will say that this script is processed by JavaScript Compressor , it is easy to recognize by the signature - the characteristic name of the function at the beginning of the script. We copy the whole source text of the script, replace the first eval with the decoder , insert it into the decoder and save it as an html-page.
<Script type = "text / javascript">
// Insert the encrypted script here, in advance
// replace all eval () and document.write () calls with decoder () in it.
Decoder (function (p, a, c, k, e, r) {e = function (c) {return (c <a? '': E ...
</ Script>
Open it in any browser and see that in textarea immediately appeared unpacked script. It's too early to rejoice, all the line shifts and code formatting have been removed. How to deal with this is written in the article about deobfuscation .
The second example. HTML-page, covered by the program HTML Protector. This is a page that demonstrates the features of the program, so all the options are there: blocking the selection and copying of text, disabling the right mouse button, protecting pictures, hiding the status bar, encrypting html code, etc. We open the source code, we look. At the very top is the already familiar document.write and encrypted script. Run it through the decoder, get the decryption function of the main content:
hp_ok=true;function hp_d01(s){ ...вырезано... o=ar.join("")+os;document.write(o) We replace the last document.write with the decoder in the function and insert after it all the three remaining encrypted scripts:
<Script type = "text / javascript">
// Insert the encrypted script here, in advance
// replace all eval () and document.write () calls with decoder () in it.
Hp_ok = true; function hp_d01 (s) {.... o = ar.join ("") + os; decoder (o);
Hp_d01 (unescape ("> QAPKRV% 22NCLEWC ....
Hp_d01 (unescape ("> QAPKRV% 22NCLEWCEG? HctcQa ...
Hp_d01 (unescape (">` mf {% 22`eamnmp?! DDDDDD% 22v ...
</ Script>
For convenience, the article does not provide complete scripts, you must copy them entirely. We open the decoder in the browser and see the protection scripts added by the program, and the decrypted original text of the page. For convenience, you can decrypt only the third script, which contains the html-code of the page. That's all the protection. As you can see, nothing complicated. Similarly, other protection of html-pages are removed.
Software for Trojan and other malicious code research
For more complex cases, heavy artillery will have to be used. This is a free Malzilla project designed to investigate trojans and other malicious code. Since all programs designed to protect copyright are uniquely malicious, Malzilla will help us in the fight against them. Download the latest version, unpack it, start it. Open the second tab Decoder, in the top window we insert the code of the encrypted script, we press the button Run script.
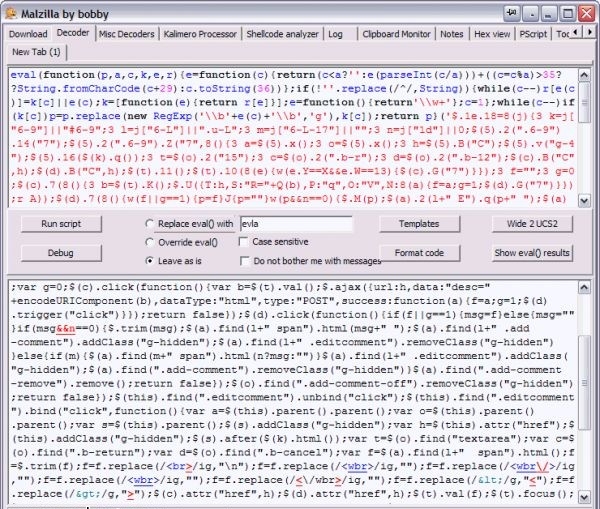
Malzilla at work
In the folder eval_temp all the results of eval () functions, including intermediate functions, are added. You can see them by clicking on the Show eval () results button, the text will open in the lower window. It can be copied, pasted into the upper window and immediately formatted by pressing the Format code button. In addition to the decoder, Malzilla also has many tools and settings to easily remove any protection from JavaScript scripts.
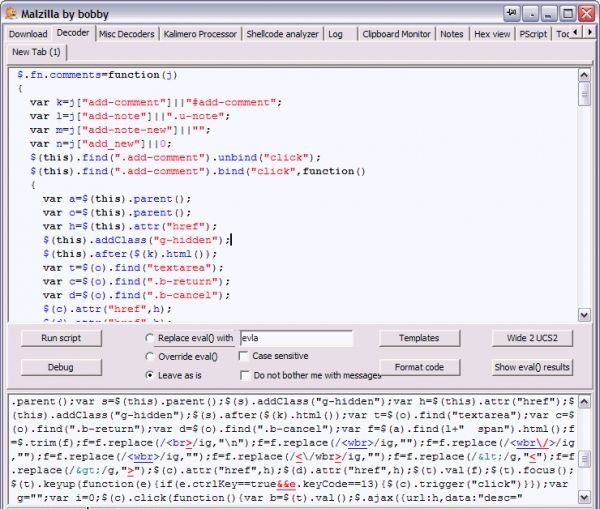
The script was successfully decrypted and formatted
Also you can pay attention to one more free tool for working with encrypted scripts - FreShow .
Decoding <? Php eval ( gzinflate ( base64_decode ( ' encoded text ' )))); ?> - option 1 (script)
Faced just now with the task as though to open secret coded through <? Php eval ( gzinflate ( base64_decode ( ' encoded text ' )))); ?> Php code.
As always, for a clue I decided to turn to Google. The answer was always found.
Code:
<Html>
<Body>
<! - beginning of decryption ->
<? Php
$ Str = gzinflate (base64_decode ('encoded text'));
While (1) {
If (($ pos1 = strpos ($ str, 'eval (')) === FALSE) {
Break;
}
$ Pos2 = strpos ($ str, ');');
$ Newstr = substr ($ str, $ pos1 + 5, $ pos2- $ pos1-5);
Eval ('$ str ='. $ Newstr. ";");
}
Print $ str;
?>
<! - end of decryption ->
</ Body>
</ Html>
Save this file as you like, fill it to the host, or run it on localhost and copy from the source everything that is between the tags
<! - beginning of decryption ->
...
<! - decryption end ->
All. The code is decrypted.
Decoding <? Php eval ( gzinflate ( base64_decode ( ' encoded text ' )))); ?> - option 2 (script)
In this case, you need to do the following:
- Save this file as decrypt.php
- Keep the encrypted code as coded.txt
- Create an empty decoded.txt file (if you run the file on the server, then specify it CHMOD 0666)
- Run the decrypt.php file
- The decoded.txt file should now contain the decrypted PHP code.
Code:
<? Php / * Taken from http://www.php.net/manual/de/function.eval.php#59862 Directions: 1. Save this snippet as decrypt.php 2. Save encoded PHP code in coded.txt 3. Create a blank file called decoded.txt (from shell do CHMOD 0666 decoded.txt) 4. Execute this script (visit decrypt.php in a web browser or do php decrypt.php in the shell) 5. Open decoded.txt, the PHP should be decrypted if not comment below http://danilo.ariadoss.com/decoding-eval-gzinflate-base64-decode/ * / Echo "\ nDECODE nested eval (gzinflate ()) by DEBO Jurgen <[email protected]> \ n \ n"; Echo "1. Reading coded.txt \ n"; $ Fp1 = fopen ("coded.txt", "r"); $ Contents = fread ($ fp1, filesize ("coded.txt")); Fclose ($ fp1); Echo "2. Decoding \ n"; While (preg_match ("/ eval \ (gzinflate /", $ contents)) { $ Contents = preg_replace ("/ <\? | \?> /", "", $ Contents); Eval (preg_replace ("/ eval /", "\ $ contents =", $ contents)); } Echo "3. Writing decoded.txt \ n"; $ Fp2 = fopen ("decoded.txt", "w"); Fwrite ($ fp2, trim ($ contents)); Fclose ($ fp2); ?>
Upon decrypting the source code I detected that the freeware application was downloaded spyware on a site. I have read this article in order for others to be able to investigate and use malicious code on their websites. I hope this helped some of you and I will endeavor to continue to the useful and insightful entries from now on.
Decoding <? Php eval ( gzinflate ( base64_decode ( ' encoded text ' )))); ?> - option 3 (online)
How to decode the code and remove commercial links from paid and free scripts?
Case one:
eval(base64_decode ('SGksIG1hbg==')); If we meet the line eval (base64_decode ('SGksIG1hbg ==')) ,
Then we go on
On the online decoder, we insert into the form only SGksIG1hbg == from our line and press the button "Decode data".
The second case:
eval(gzinflate(base64_decode ('80jNyclXyFTPVUhJTc5PSU0BAA=='))); If we encounter the line eval (gzinflate (base64_decode ('80jNyclXyFTPVUhJTc5PSU0BAA ==')));
,
We go already on
And we paste the whole line in the form starting with eval (gzinflate and ending )));
And click "Decode".
<? Php eval ( ( base64_decode ( ' encoded text ' )) - option 4 (using echo)
To decipher malicious inclusions in the php code type:
eval(base64_decode(”DQplcnJvcl9yZXBv...tPWhlYWRlc...2F0aW9uOiBodHRwOi8...eGl0KCk7DQp9Cn0KfQ0KfQ0KfQ==”)); You can simply replace the function eval with the echo function and see what happens.
This is one of the most basic ways to decrypt base64_decode ...
If none of the ways helped, then it's not destiny

If you have met any other solutions to this problem, write to the commentary, try to understand them.


Comments
Commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.