MicroJoyner for Beginners
Joiner - Eng. Carpenter. From the English. Join - bond, bind. This name was given to a class of programs intended for connecting several executable files.When the knowledge was not enough, I personally used such programs to start ICQ and Web-browser simultaneously with a single click of the mouse (I repeat: when the knowledge was not enough, now I think that it is more correct
Use scripts). But more often such programs are used in not completely law-abiding purposes: Bind malicious programs with ordinary ones. The goal is to make, for example, vparivanie their "Trojans" invisible or less noticeable. For example, a compiled pinch does not normally produce any messages at startup.
The person who launched the file and did not see anything on the screen can become very suspicious. If, after launching the program, he sees, for example a photo, suspicion can be much less. But this
lyrical digression. Joiner (sometimes written by Joiner) works as follows: when you start the program, you select the files that you want to connect, after the end of the work, a file is created at startup, which will start all the files you selected at the beginning of the work.
For example, there are files 1.exe and 2.exe , as a result of work the file 3.exe will be created. If we run this file (even copying it before this to another folder) then two programs will start up: 1.exe and 2.exe.
What can a jointer do: gluing at least two files (in principle, this is enough if you need to connect, for example, 3 files: 1, 2, 3, then first glue 1 and 2 in 4, and then 4 and 3 in 5, eventually at start 5 Files 1, 2, 3 will be started). Very often the jointer can only glue the executable files (with the extension * .exe), but this does not always happen.
One of the most popular and famous joins is the MicroJoiner from coban2k (the author of the Trojan Pinch, which you can read here on the forum). Current version 1.7. There is a version of the program with the Russian interface. Actually, we will consider it for practice.
To start the program (taken from the program page):
- glues up to 4096 files
- glues files of any types (ie images, icons, program documents, etc.)
- the ability to select the icon for the resulting file from icon files (* .ico), executables (* .exe), dynamic libraries (* .dll)
- glued files are encrypted (antiviruses can not determine which files were glued together)
- the resulting file can be compressed by the built-in packer (reduces the file size, the compression ratio is about the same as that of zip)
- small bootloader (only 2048 bytes)
- the created file can be compressed by an external packer
- for each file you can install additional options
- the ability to register DLL (OCX), which you may need for programs written in Visual Basic
- operations on the glued file itself (Melting, about this below)
- Works under Windows 95/98 / 2k / XP / 2k3
- Supports drag-n-drop (it is more convenient to add files, you can simply drag the added files to the jointer)
- Support for the interface XP (in my opinion, this is superfluous, but once it is written - translate)
- it is possible to save and load projects
- there are versions in English and Russian languages
The program itself can be downloaded [ here ].
At start we see here such window
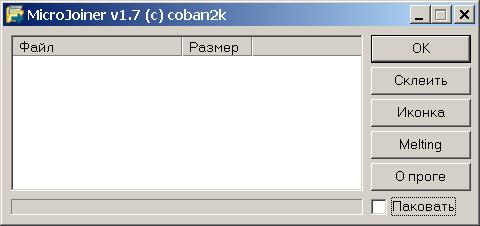
On the left is a white box, in which there is a list of glued files. You can add files simply by dragging them from the window of any program, or by right-clicking on this field and selecting add files.
A little about the context menu items:
- Add files - opens the standard file selection dialog, after selecting the file is added to the list
- Project - allows you to save and load settings (selected files, and options for each file), I personally use very rarely
- Delete files - deletes the selected files from the list
- Clear - deletes ALL files from the list
- Advanced - opens a window with additional options for the file. By adding files, we can proceed to configure additional options for those files that need it.
Advanced Settings Window
Contains the following configuration blocks:
Visibility :
Hide the window - the window of the program being launched does not appear on the screen
Maximize - the program window will be expanded to full screen
Minimize - the program window will be minimized in the button on the taskbar.
When using malicious programs, this group is almost irrelevant, since the programs that should be hidden usually do not have a window. But, for example, it can be useful for documents or pictures.
Attributes of the file :
- Archive
- The Hidden
- Read Only
- The system (System)
The unpacked file will be assigned the attributes of the corresponding selected items. I note that by default, Hidden and System files are not displayed in the explorer (and other programs). So the choice of these options can be useful.
Other
Do not run (Copy) the file will be simply extracted , but it will not be launched for execution. This can be useful, for example, in such cases: if you are registering the program at startup and you need it to start only the next time you start the system.
A unique filename for the file will generate a random name from numbers and letters. Personally, I do not recommend using this option, because the name like ope23r76C.exe when browsing the folder immediately catches your eye and causes suspicion. Better before gluing, rename your file to a more plausible name.
Wait for completion - the following files in the project will be extracted only after the completion of this program, or after closing the window with a document or picture. Here it is worth noting that the files
Are unpacked from bottom to top , i.e. First unpack those files that are lower in the list of files, and then in the order from bottom to top. So the order of the files can sometimes matter .
Command line parameters - enter here the parameters without the program name, if your executable file requires them to work. Say, if program format.com , you can enter into the parameters: C: / q (This is just an example, there is no real use)
Run from:
The ability to specify the folder to which the file will be extracted, and from which it will be sent for execution. For some programs, the working directory is a fairly important variable. It does not matter for a picture or a document. But if you need to run the Trojan, it's best to do it from the Windows, System or System32 folder.
Temp - a subfolder will be created in the temporary folder directory where the file will be extracted.
The system folder will be extracted to the system directory, usually % windir% \ system32
Windows folders, too, but in the folder% windir%
The current folder will be decompressed to the folder from which the glued file is launched. Be careful: if the folder is not writable (for example, on a CD-ROM), the file is created and will not run.
You can specify the folder path to a folder manually, but it is recommended that you have an understanding of the structure of disks and directories on the user's computer. A folder with Windows is not always called that, and is not always on the C: drive.
Melting - this option affects the actions available for selection if you decide to take advantage of the file management feature (see below).
Select file for Melting'a this option can be installed only on one file in the project. If previously you selected it on another project file, it is automatically removed from the previous file.
Add to autorun - the file is written to autorun to the registry at HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ Curr entVersion \ Run with the parameter name equal to the file name.
Register DLL, OCX - the item is used to register the required libraries.
Let's return to the main window. To the right of the file list are the operation control buttons.
OK - closes the program.
The paste creates the file Joined.exe in the folder with MicroJoiner in accordance with the project settings. This file is the result of the program. It is at its launch that unpacking or launching of glued programs will occur.
Icon - the button allows to select the icon for the file Joined.exe. There is only one advice - try to make sure that the icon corresponds to the content. For example, if you glue your Trojan with a picture, then make a jpg file icon, if with a Word document - with the corresponding icon. Icons can be selected from both files
* .ico icons and executable files * .exe, * .dll.
Melting - opens the window for selecting operations on the file. By default, the option Do not use Melting is set ; No action will be taken.
Delete the resulting file (Self-destruct) - after the startup, the file-splicing will unpack and run the necessary files, and then it will be deleted. The disappearance of the file can cause suspicion !!!
Other options will be available only if you have checked the "Select file for Melting" option on one of the project files.
Replace the resulting file with the selected file and Delete p. File and copy the selected file to the same folder - in both cases the file-splice will be deleted. But in the first case it will be replaced with the file chosen for Melting (ie the new file will receive the same name as the file-glueing), and in the second the selected file will be copied to the folder with the original name.
As you can see the program has the capabilities of a mini-installer. Although it is usually established by it is not quite legitimate programs. Because of this use (although it was created for this), antiviruses unable to determine what is inside the glue (you do remember, the file is encrypted) added the program to their databases. So now any, even the most harmless files glued together by this program are defined by antiviruses like Win32 / TrojanDropper.Microjoin.C ( variations are possible, it depends on the antivirus).
What should be understood as "The tool for steaming Trojans for the Win32 platform known as MicroJoiner". This does not mean that your file is infected or that the program adds its Trojan. It's just that way, antiviruses try to protect users. Because of this fuck of Security Advocates, the program is difficult to use on its own. Although if for peaceful purposes - an executable file made by you for you, it is possible to add to the list of exceptions to antivirus. The program considered has the most ample opportunities among the joins. If you have to deal with another program, the essence of the work does not change, although you may not find some convenient options.
A small collection of various joinners can be found on this page (http://joiners.narod.ru/Html.htm). All of them are known for a long time and just as MicroJoyner is defined by antiviruses. Therefore, the restrictions on their use are the same ..
I hope you could find something useful for yourself here.




Comments
Commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.