We break the soap, use BrutusAET2
THE MATERIAL IS PUBLISHED FOR FAMILIARIZATION. THE AUTHOR DOES NOT HAVE ANY RESPONSIBILITYAnd so, I want to tell you: how to steal a soap (e-mail) with the help of BrutusAET2.
Let's start.
We will need :
1) The program for brute force passwords BrutusAET2, which can be downloaded from here:
• http://www.hoobie.net/brutus/brutus-aet2.zip
2) Dictionaries that you can take from here:
• http://www.passwords.ru/dic.php
• http://www.insidepro.com/eng/download.shtml
• http://www.outpost9.com/files/WordLists.html
• http://www.acolytez.com/dict/
• http://www.phreak.com/html/wordlists.shtml
• http://www.mobilstar.ru/files/dict/
3) Straight arms.
For example, I will result in the hijacking of a soapbox at @ yandex.ru.
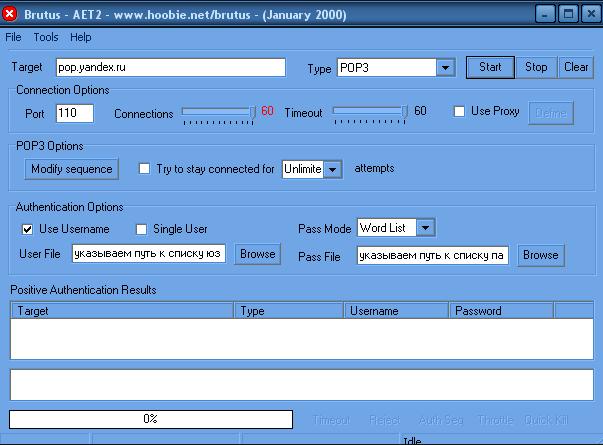
Configuring the program for brute force passwords BrutusAET2:
1) Have opened the program.
2) In the Target field we write pop.yandex.ru
3) In the Type field, select POP3
Connection Options:
1) Port we put 110.
2) Connections set to a maximum of 60.
3) Timeout set to a maximum of 60
POP3 options:
Do not touch =)
Authentication options:
If we want to cram the list of mnogolnikov , then we need to create a textbox, call it users.txt, it means throws down the lists of users.
For example:
Vasja_pupkin
Abcdefgh
Abcabc
We climb in the program there tick the Username.
Use Username: we specify a way to the list of users.
Let's move on to the password list ...
We create a textwriter words.txt and then we shove passwords.
For example:
Password
Pass
123
We climb into the prog and choose
Pass mode : Word list
Pass file : specify the path to the password list.
It's also easy to break the soap with mail.ru just put it in Target: pop.mail.ru and the rest is the same.
In general, everything should look like in the screenshot:
Some useful links from me ...
Hashi: decrypt passwords
"Press once to show the spoiler - click again to hide ..."
Http://passcracking.com/
Http://us.md5.crysm.net/
Http://www.plain-text.info/
Http://gdataonline.com/
Http://www.milw0rm.com/md5/info.php
Http://md5.t145.1paket.com/md5crack.php
Http://www.securitystats.com/tools/
Http://md5.rednoize.com/
Http://md5crack.it-helpnet.de/
Http://passcracking.ru/en/index.php
Http://ivdb.org/search/md5
Http://www.xmd5.org/index_en.htm
Http://ice.breaker.free.fr
Http://shm.hard-core.pl/md5
Http://www.hashchecker.com/?_sls=add_hash
Http://md5.benramsey.com
Http://md5.xpzone.de
Http://www.csthis.com/md5/index.php
Http://www.schwett.com/md5/
Http://www.xeons.net/genesis
Http://md5.geeks.li/
Http://www.tmto.org/?category=main&page=search
Http://www.md5database.net/
Http://www.md5decrypter.com/
Http://www.securitydb.org/cracker/
Http://alimamed.pp.ru/md5/
Http://www.hashreverse.com/
Http://md5.overclock.ch/biz/index.php?p=md5crack&l=en
Http://rainbowtables.net/services/results.php
Http://0ptix.co.nr/md5
Http://www.md5this.com/component/opt...pper/Itemid,8/
Http://shm.pl/md5/
Http://www.cmd5.com/english.aspx
Http://www.md5encryption.com/
Http://www.eus.ru/md5/?md5e=&md5
Http://www.thepanicroom.org/index.php?view=cracker
Http://rainbowcrack.com
Http://www.antsight.com/zsl/rainbowcrack
Http://www.und0it.com/
Http://md5.overclock.ch/
Http://www.panpan.org/2006/md5asp/HOME.ASP
Http://www.bisix.tk/
Http://www.md5hashes.com/
Http://md5.mmkey.com/home.asp
Https://www.astalavista.net/?cmd=rainbowtables
Dictionaries:
"Press once to show the spoiler - click again to hide ..."
Http://www.mobilstar.ru/files/dict/
Ftp://ftp.funet.fi/pub/unix/security/dictionaries/
Http://www.phreak.com/html/wordlists.shtml
Http://tpircs.anarxi.st/passwd.txt
Http://www.acolytez.com/dict/
Ftp://ftp.openwall.com/pub/wordlists/
Ftp://ftp.ox.ac.uk/pub/wordlists/
Ftp://coast.cs.purdue.edu/pub/dict/wordlists/
Http://www.passwords.ru/dic.htm
Http://getfile.biz/15660
Http://www.outpost9.com/files/WordLists.html
Ftp://ftp.cerias.purdue.edu/pub/dict/
Http://www.insidepro.com/eng/download.shtml
Http://www.insidepro.com/eng/download.shtml
Http://www.passwords.ru/dic.php
Http://neworder.box.sk/codebox.links.php?&key=passdict
Http://acolytez.com/dict/
Http://dim-ok.jino-net.ru/ps.tar.gz
Http://advlamer.narod.ru/manual.htm
Http://forum.antichat.ru/thread5087..2%E0%F0%E8.html
Http://forum.antichat.ru/thread5101...2%E0%F0%E8.html
Http://forum.antichat.ru/showthread.php?t=10814
Http://forum.antichat.ru/showthread.php?t=5493
Ftp://ftp.funet.fi/pub/unix/security/dictionaries/
Http://www.phreak.com/html/wordlists.shtml
Http://tpircs.anarxi.st/passwd.txt
Http://www.acolytez.com/dict/
Ftp://ftp.openwall.com/pub/wordlists/
Ftp://ftp.ox.ac.uk/pub/wordlists/
Ftp://coast.cs.purdue.edu/pub/dict/wordlists/
Http://www.passwords.ru/dic.htm
Http://getfile.biz/15660
Http://www.outpost9.com/files/WordLists.html
Ftp://ftp.cerias.purdue.edu/pub/dict/
Http://www.insidepro.com/eng/download.shtml
Http://www.insidepro.com/eng/download.shtml
Http://www.passwords.ru/dic.php
Http://neworder.box.sk/codebox.links.php?&key=passdict
Http://acolytez.com/dict/
Http://dim-ok.jino-net.ru/ps.tar.gz
Http://advlamer.narod.ru/manual.htm
Http://forum.antichat.ru/thread5087..2%E0%F0%E8.html
Http://forum.antichat.ru/thread5101...2%E0%F0%E8.html
Http://forum.antichat.ru/showthread.php?t=10814
Http://forum.antichat.ru/showthread.php?t=5493
Links !!! All references to the world !!!
Methods for finding passwords for beginners
Method number 1. "Brutus" / long /
The first method we will have brute (Brute Force) - a method of full search.
What you need:
1. The program for busting BrutusA2 (WWWHack or similar)
2.Knat the address of incoming mail (pop3) mail service. This address can be found in the help or faq sections on the mailer's website.
3. Also desirable is the Passwords List
..
Pros: the password will always fit! (If not in the dictionary, then a complete search)
Cons: to get it guaranteed - it may take several millennia or millions of years.
..
Recommendations:
Since busting is the longest way, and in order to cut it somehow, it is necessary:
A. Go and register yourself a box on the postal service that you will crochet. When registering, pay attention to the "Password" field. Your task is to learn the requirements of the mail service to the minimum and maximum length of the password, and the symbols used (next to the field it is usually written).
B. Open the password dictionary (I prefer Raptor for such purposes), sort the dictionary by the length of the password (from shorter to longer), remove passwords that do not fit the requirements of the mail service in length, and with forbidden characters.
C. Use data from the "Collection of information" method (see below)
..
Help for those who do not have the Internet:
Brute Force (Conversation: Brutus Translation: Brute Force) - password selection by brute force. Example for "Direct bust":
Aaa
Aab
Aac
...
Zzx
Zzw
Zzz
etc.
Example for browse "By dictionary":
Abila
Abott
Abitz
Admin
etc.
Those. Since many people use meaningful and easily remembered words to remember the password, why do we need to sort through the characters for a long time, if it is faster to sort through the words?
Ps Where what to take (mentioned in the method):
BrutusA2 -> http://www.hoobie.net/brutus/brutus-download.html
Raptor -> http://madmax.deny.de/products/raptor/download.htm
Pss About passwords that are often chosen - in another, separate, article.
Method number 2. "Collecting information" / requires care /
What you need:
Search Engines:
Http://google.com
Http://ya.ru
Http://rambler.ru
Http://aport.ru
Http://yahoo.com
How to do:
We kill our soap in search and look where it occurs. We go and find everything (where it occurs, on what site, what he wrote and what he asked, when, under what login) we copy and store in a notebook for further analysis.
After that, we analyze and make general conclusions about the interests of the person, trying to substitute the password for the found (year of birth, nickname, name, interests, etc.).
..
Recommendations:
To search it is necessary on all search engines as on full soap [email protected] and only by login my_email
Getting to the Forum (having found his login (nickname)): we right-click on the image of his Avatar and look at the path of this image (and suddenly he did not upload it to the Forum, but used his lying on his site? (Although he could take a stranger )). Also click on his profile and all that is there - also copy into Notepad (there may be the number of Aska and year of birth, interests, etc.). Do not forget in the profile (if there is) click on the link "Find all user's posts". Carefully read. Maybe there will be some clue (keeping the "Secret Question" in my head). All informative and distinct from "Gyg", "Lol", etc. - in Notepad.
If we find his second soap - we go through the search engines once more.
The same goes for Aska (around the search engines). With ICQ, do not forget to glance at [forbidden link]
Also do not forget to look for soap and nickname at http://www.icq.com
If he has the original nickname - AmSuPerrR, also go for the search engines. Simply if he has a standard nickname - Alex, then you are unlikely to sort out 12 million pages quickly (though - using the syntax of search queries and sorting out "search in the found" you can try).
When you have in your notebook, perhaps a decent list of information, start from it to create a pass-list for this user. And: the year of birth should be tried to substitute in different formats. For example, you found that the year of birth 01.01.2005
Try these options:
01012005
010105
112005
1105
Also try the options (where my_email is its login):
My_email2005
My_email05
Or:
Hisname2005
His name is 05
etc.
To substitute it is simple. Just copied into Notepad "decomposed" according to the words in the column, and try on each found to write a few options. And after that you can use the "Brutus"
Also you check the found "second soaps" on the subject whether they exist or not. It may turn out that they were registered long ago, and then the need for them was gone. Then register it for yourself, and try to restore it to the password from the Forums, chats, directories, etc.
Method number 3. "Password recovery" / sometimes effective /
How to do:
First, we climb to the postal service and click on the link "Forgot password!" (Or similar). We look at what there is a secret question.
For example, if he is "My favorite dish", then the girls can try to substitute the word - ice cream
If the "Year of birth of the grandmother", "Passport number", "Mother's maiden name" - then try 111, 123, 12345, the year of birth of the one whose password is "reminiscent", maybe the answer is the year of registration of soap, well, etc. Since not often there are those who know the year of birth of the grandmother and remember the maiden name of the mother. With the passport number is more difficult, since some really take it and drive it straight. But still try 111, 123 ...
Also you can be great here with the data collected in the method "Collection of information."
Added (Eco [L] og):
Sometimes a secret question can be of the type here: 1234567qwerty
Then, in some cases, and the answer to it can be 1234567qwerty
Or similar, typed by the method "on the clave from the bald" (to pick up this will be almost not realistic)
Method number 4. "Recovery from another service" / in a hurry and the password from soap you can take, and the forum / chat /
The whole point is that the password for soap is harder to pick up than the password from the Forum, chat, dating service, liv.jurnala, etc. Those. From those places visited or visited by one whose soap is "restored". Hence - bypass all sites, forums, etc. Which fell into our field of vision with the method of "Collecting information." We look at what there, for example, for the Forum and already reduce our task to finding vulnerabilities to this Forum (using the same google.ru)
We have a chance (not great, but there is a chance) that the password from the Forum is suitable for soap as well.
Method number 5. "Trojan" / demanding skill /
The method speaks for itself. The task is to reduce to Trojan's floatation or some kind of Keyloger thread (which you, accordingly, should have), and the expectations from them of reports (logs).
Here for vparivaniya well help methods "Vulnerability software" and "SI / Social Engineering /"
Method number 6. "Vulnerability of software" / requiring knowledge /
This is probably more of an auxiliary method for the Trojan method. It takes a lot of effort to get Troyan to vanish. But it will be easier if you know the operating vulnerabilities in the software. The same browsers, mail programs (Outlook, TheBat !, etc.), maybe ICQ. Then your task will be reduced to vparivaniyu links to a thread of your site, when you visit the visitor through a vulnerability in the browser to boot and run Trojan. Or the premise was "hurried up" the letter.
Method number 7. "Vulnerability of mail services" / also requiring knowledge or ability to use the search engine /
The method directly concerns the vulnerability of email services. They sometimes come up from time to time. Starting from the sending of the letter, when viewing the user's browser, which thread settings will be changed, and until the recent phint with the interception of the password change package of its mailbox, changing its (package) and changing the password for the desired box. Well, etc.
Method number 8. "Have hundreds of rubles, friends will wait" / an invoice. Requires a job and a wm-wallet /
You go on okolohakersky site and ask for an entitlement to "remind" the password. But then be careful when paying, since I got divorced a lot of throws (yes that there divorced - they always were).
..
Recommendations:
Never transfer payment by Advance (100% guarantee that the password will be "remembered" by no one (more precisely - some people can give it, but they will be spared when you pay them - before or after. And they, basically, take it after the order is fulfilled .))
As evidence, do not be led that the letter was sent from the box you need.
Also, do not immediately start when the proof is according to the scheme:
You send any letter to the desired box, and then you (after some time) send the text of this letter.
As a protection against a thrown, you can use the scheme "through the Guarantor" or the scheme that is above, but slightly corrected:
1.You agree when you are both online.
2. You are on the "required" soap you send out a thread of text and you should immediately tell what text you sent.
Then at least there is a guarantee that something soap is under control. But with the transfer of money - yourself agree.
Method number 9. "Do not have a hundred rubles, but have a hundred friends" / the ability to make acquaintances /
Just have a good friend (administrator, support, or, better, director) working either to the office where the soap is, or providing a hosting / internet office where soap.
Well, or someone familiar from a thread of the FSB, FAPSI, Office "K" (R) who at risk, will exceed his official authority, find out the password from the support of the postal service and tell you.
This is a very bad and wrong method. And it is almost very rare (and thank God)
Either have a friend - admin Forum, chat, etc. Where the person is sitting. If you are not familiar, nothing hinders you as a thread to get to know him ...
Method number 10. "SI / Social Engineering /" / The most accurate method. Requires the ability to set a task, analyze. Training /
Many of the methods described before, somehow then reduce and intersect with this method. The same thing - for this method some of the other methods (such as "Collecting information", "Vulnerability of mail services" etc.) are required,
This is the most extensive and branched method. Therefore, right now, briefly, and then put in a separate article.
The general idea is that you need to know the password from the soap directly from the owner. Or to persuade him to commit any actions you need (the same guaranteed launch of Troyan).
Under the "learn directly from the owner," it is understood that this owner will tell you the password himself. " But he does not even understand that he himself did not know whether he gave it to him (or he may understand, but then).
Ps About the SI method and its sub-methods - in the next. Article (if there is a desire and interest)
Method number 11. "What for he is so needed?" / A long but relatively simple method /
The essence of the method is to force the owner to abandon the mailbox voluntarily (sometimes it is necessary to "restore" not to read, but to have the right box). And it's easier to do this - just periodically spam this box. If the owner of the box is not too shy how to get rid of this spam, then in a couple of weeks he will get tired of shoveling out of the box or cleaning it from a ton of letters and he will abandon it. And postal services are not rubber. And when there is a limit on the location for the box and when it is not visited, then such a box will eventually be removed.
Well and lastly an alternative method
Method number 12. "Fear" / criminal /
You catch the master in the doorway ...
By antichat.ru




Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.