Attack with your time server: NTP amplification attack (CVE-2013-5211)
On January 13, the US Emergency Command Computer (US-CERT) issued a warning about a new method of DDoS attacks.
Infected computers send a monlist request with a fake IP address of the sender to the NTP server.
The query monlist returns a list of the last 600 ntpd clients.
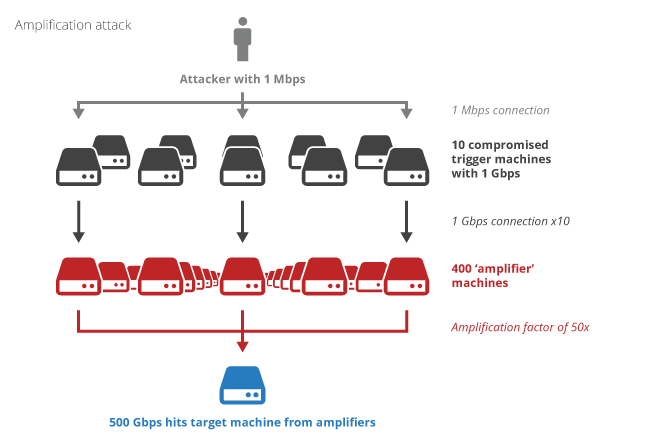
Thus, a small request from the infected computer to the victim sends a large stream of UDP.
This is the essence of amplification.
An unprotected NTP server becomes an unwitting intermediary of the attack.
Attacks are subject to versions of ntpd to 4.2.7p26 (stable now 4.2.6p5).
To test your server for the vulnerability, you can run the following command:
ntpdc -c monlist адрес_сервера If the command lists the clients (and not "timed out, nothing received"), then the system is vulnerable.
Elimination
Now there are at least 3 ways:
- 1) Update ntpd to version 4.2.7p26. In FreeBSD, update the ports and install ntpd from net / ntp-devel.
Without an upgrade, you can:
- 2) Disable the monlist in ntp.conf by adding the line
disable monitor - 3) Or disable any server status queries in the restrict
restrict default kod nomodify notrap nopeer noquery
restrict -6 default kod nomodify notrap nopeer noqueryrestrict default kod nomodify notrap nopeer noquery
restrict -6 default kod nomodify notrap nopeer noquery
Perhaps you did not know at all that your NTP server is visible outside (- :.
Then disable access to it completely.
I ran into this problem back in November, when NTP traffic on my public NTP stratum1.net became 30GB per hour.
I noticed this not immediately, tk. Even on the Atom processor, the load was less than 5%.
Then I wrote a bash script that looked at the traffic statistics of the boundary firewall over the last half hour (via netflow) and automatically added a deny rule for too active clients. And after two months it became clear what it was.
Sources:




Comments
Commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.