Fraud in spam (letters of joy)
The word "spam" often means only letters of an advertising nature, but this is not entirely true: spam of some species is sent for a different purpose. To such "non-commercial" spam, in particular, one of its dangerous varieties is fraudulent letters.
Spam technologies allow organizing mass mailing of fake messages, substituting false addresses of senders and using infected computers of unsuspecting users for distribution. It is not surprising that this attracts scammers and cybercriminals of different calibres: the specificity of spam creates conditions for deceiving users, and for hiding the traces of criminal activity.
It contributes to the criminalization of spam and the fact that the originators of mailings are not easy to find because of the anonymity of the messages being sent, which means that cybercriminals can count on impunity. Spammers are actively used by sellers of counterfeit or counterfeit products, criminal service providers and virus writers.
This article will deal with fraudulent spam emails sent out to entice recipients of money or access to confidential data that can be used to steal users' money.
Phishing
The most dangerous variant of fraud using spam is phishing .
With the help of phishing mailings (English phishing from fishing-fishing) spammers try to get personal user data: logins, passwords (usually to online payment systems), credit card numbers and PIN-codes in order to use them for profit later on . The most frequent targets of phishing attacks are users of Internet banking and payment systems.
Phishing emails simulate messages from reputable organizations (banks, financial companies, payment systems). Typically, such letters contain a link to a counterfeit page and, under one pretext or another, urge the recipient to enter his personal data, as a result of which they are in the hands of scammers. In order for the victim not to guess about the deception, this page is designed in the same way as the site of the organization on behalf of which the message was sent (the sender's address is also forged).
In some cases, after the introduction and sending of data, the user's browser was redirected to this site, as a result of which the victim's chances of suspecting the wrong were reduced to almost zero.
Sometimes the user does not fall on a fake site, but on a page infected with an exploit. Using a software vulnerability, an exploit installs a Trojan program on the user's computer that collects various information (for example, about access codes to accounts) and sends it to its "owner." In addition, the machine thus infected can become part of a zombie network and used to carry out cyber-attacks or send out spam.
To deceive those who nevertheless pay attention not only to the appearance, but also to the addresses of the sites visited, the phishers mask the used URLs, trying to make them more like the original ones. The phishers started to register on the free hosting of domain names similar to the names of the domain names of the sites of the attacked organizations, however, over time, more and more sophisticated methods began to be applied to this purpose.
A typical kind of disguise can be seen in the following letter, targeting PayPal customers:
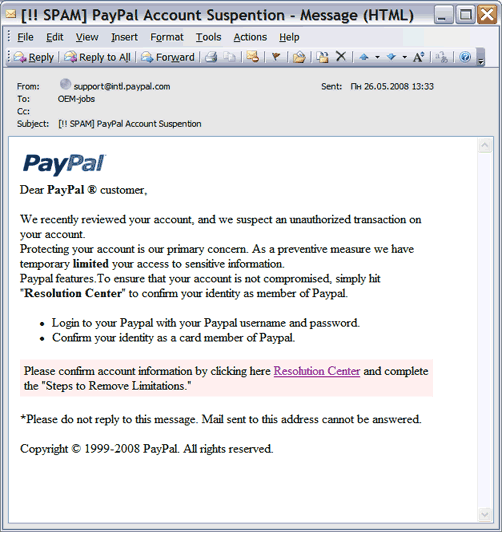
Only a very attentive person, by hovering the cursor in the letter, can notice that the link actually leads to the phishers website. The link is very similar to the address of a legitimate site, but the domain to which the user hits is quite different: client-confirmation.com.
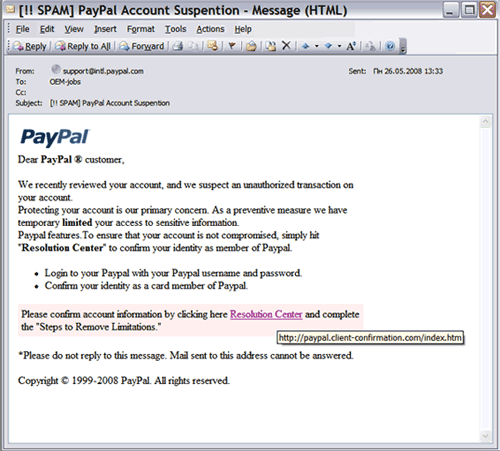
In this case, the "wrong" address will be displayed when you hover the cursor over the link in the letter, so that an advanced user is able to recognize the forgery even before clicking on the link.
There are also more primitive variants of deception. The user allegedly on behalf of the administration or the technical support service of a service receives messages in which under different pretexts it is urgently suggested to send a password from his account to the address specified in the letter - as a rule, under the threat of closing this account.
On the Runet, this technique is used by phishers mainly to gain access to users' mail accounts. It is worth noting that, by monitoring the user's mail, scammers through password reminder systems can acquire and its registration data on other Internet services.
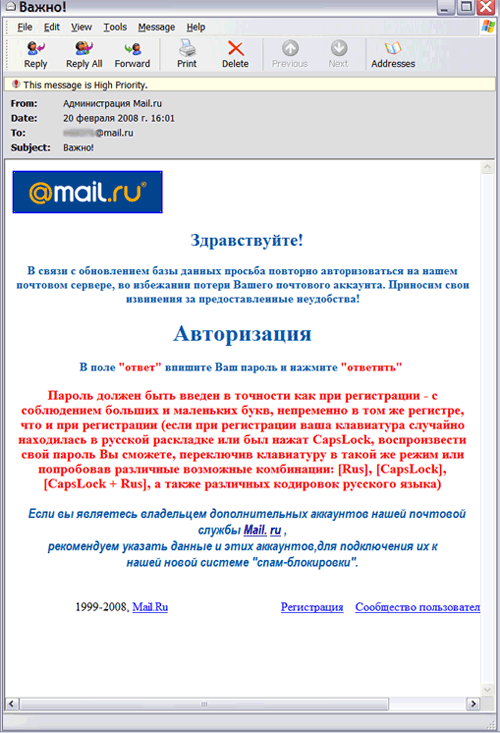
Another common method of collecting passwords for mail is sending emails in which everyone is invited to use the "vulnerability in the password recovery system", using which, it is possible to find out the password of another user. To gain access to someone else's account, the recipient of the spam message must send the login of the future victim, as well as his password, to a certain address in a certain format. Need I say that the victim of intruders is the "hunter" himself, who took advantage of the questionable proposal?
However, over time, users realized that serious companies never ask for passwords to be sent in emails, and the effectiveness of such traps began to fall. So now spammers have to carefully mask the forgery letters, as a result of which it becomes more difficult for recipients to distinguish them from legitimate messages.
Typically, the targets of phishing attacks are Western payment systems and banks with advanced online banking and a large number of customers who use them. However, with the development of online banking in RuNet, phishers are increasingly conducting attacks designed primarily for Russian users.
One typical example is phishing attacks on Alfa-Bank customers. Fraudsters worked according to the classical scheme: the electronic messages they sent were imitated by letters from the administration of the bank and contained a link to a fake site on which the user was asked to enter their login and password for access to the Internet banking system. The appearance of the page was an exact copy of the main page of the site of Alfa-Bank. In addition, scammers prepared a careless user an unpleasant "gift": when clicking on the user's computers, a malicious program was downloaded. Similarly, attacks were carried out on users of WebMoney and Yandex.Money systems; Several times was the target of Citibank's phishers.
|
Attackers also often try to access mail accounts of users, requesting their logins and passwords on behalf of the administration of Russian postal systems.
Spoof money with spam
In addition to phishing, Internet scammers use a variety of other techniques that allow spam to lure hapless users into traps and to rob them. Most often spammers try to play on the naivety and greed of their potential victims, which, incidentally, is characteristic of all scams. To achieve their goals, scammers use various schemes, and the most common of them we will consider in more detail.
Nigerian letters
This popular fraud scheme was developed and actively used by fraudsters from Nigeria, for which it received its name. However, at the present time, "swindle" fraud is being practiced by swindlers all over the world.
In the implementation of the classic "Nigerian" scheme, spammers send letters on behalf of a representative of a noble family (usually residing in an African country) who fell into disfavour at home due to civil war / coup d'etat / economic crisis / political persecution. In the classical "Nigerian" letters to the addressee they address in broken English with the request to help "save" a large sum of money, transferring it from the account of the disgraced family to another account. For the money transfer service, scammers promise a solid reward - usually a percentage of the amount transferred. In the course of the "rescue operation" it turns out that a volunteer (albeit not self-reliant) assistant is required to transfer a small amount, in comparison with the promised remuneration, for processing the transfer / giving a bribe / payment to a lawyer, etc. As a rule, after transferring money, any opportunity to communicate with the "widow of the former dictator" or "the son of the late disgraced minister" disappears. Sometimes the victim is forced to shell out a few more times, under the pretext that there are regular unforeseen complications.
Sometimes the sender is represented by a high-ranking official who allegedly managed to earn a large fortune with the help of bribes and fraud, but is now under investigation and can not take money out of the country. To transfer money, he must be given access to some bank account. A certain percentage of the total amount is offered for the help of the addressee. It is clear that having obtained the desired control over the credulous user's account, scammers do not leave a penny on it.
What dramatic stories are not told in the "Nigerian" letters! In fantasy, their authors can not refuse, not without reason in 2005 it was the "Nigerian" scammers who were awarded the Antinobelev Prize in Literature. Do not remain without their attention and Russian subjects: in the same 2005, typical "Nigerian" messages in English were sent on behalf of relatives and people from the inner circle of the disgraced oligarch Mikhail Khodorkovsky. On this Russian specificity came to an end - otherwise there were no differences from the classical "Nigerian" scheme of fraud.
|
Dear Friend, I am Lagutin Yuriy and I represent Mr. Mikhail Khordokovsky the former CEO of Yukos Oil Company in Russia. I have a very sensitive and confidential brief from this top (Oligarch) to ask for your partnership in re-profiling funds over US $ 450 million. I will give the details, but in summary, the funds are coming via Bank Menatep. This is a legitimate transaction. You will be paid 4% for your "Management Fees". If you are interested, please write back by email and provide me with your confidential telephone number. Please keep this confidential; We can not afford more political problems. Finally, please note that this must be concluded within two weeks. Please write back immediately. Write me back. I look forward to it. Regards, Lagutin Yuriy |
There is also a romantic version of this scheme of spam-fraud letters from "Nigerian" brides . Touching messages are sent on behalf of girls living in distant exotic countries. Photo of a dark-skinned beauty is attached. As a rule, scammers conduct target attacks - such letters are usually received by users who registered on dating sites. If a potential victim is included in the correspondence, she is told a story in the spirit of soap operas: "Relatives have been killed, they are not being released from the country, and I'm actually a rich heiress ..." In the third letter, the girl already swears in eternal love and asks to take her out of the country Together with its millions. All that needs to be done to the hero-savior is to help transfer millions of orphans from the country, and for a solid reward. Of course, the assistant needs preliminary costs, the amount of which reaches several thousand, and sometimes tens of thousands of dollars. To make the case more convincing, an imaginary pastor and a lawyer are connected to the case. At the final stage of fraud in the course are false documents.
Fake notice of winning the lottery
This kind of fraudulent spam is close to Nigerian letters . Users are sent false notices of winnings in the lottery , allegedly conducted among random e-mail addresses / phone numbers, and offers to receive "free" gifts as a prize. To be convincing in such a letter there can be a picture of the prize and all kinds of "authenticity attributes" of the lottery - ticket number, registration certificate / license and other false information. As in the previous case, to receive a win, the user under different pretexts is suggested to make a preliminary payment for a certain amount at the scammers' scores specified.
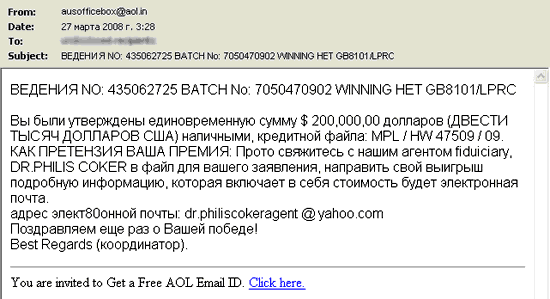
There were also Russian versions of such letters, the text of which was clearly translated from the English original with the help of an automatic translator.
The recipients of such notices should first of all remember that participation in any lottery is impossible without the user's consent. If you never gave such consent (and most likely do not know anything about the lottery in which you allegedly won), then you are dealing with a typical message from scammers who are trying to lure the recipient money, and not at all to make him happy with his winnings.
"Errors" in payment systems, magic wallets, code generators
In spam letters of this type, the user is informed that a vulnerability has been discovered in a certain payment system that allows "to make profit". Further, the essence of the vulnerability is described and a recipe for earnings is proposed, consisting, as a rule, in sending a certain amount of money to a "magic" wallet. Scammers promise that after a while after the transfer, the money will be returned to the user in doubled (tripled, etc.) quantity. Of course, this "magical" wallet belongs to scammers, and the money transferred to it for the user will be irretrievably lost. And complain the victim can not (submit a statement to the police: "I tried to hack the payment system and as a result lost money").
Subject: Interesting
|
REALLY
Hello! I want to tell you how I was deceived by 150 WMZ, but I recouped. I found on the web somewhere an article of approximately this content: "There is a magical WMZ purse in the WebMoney system, and everything you send to it will return to you in triple size! Any amount! Send a thousand - get three thousand" and .d ... I did not believe it, but my curiosity took mine and sent $ 5 for the test. After checking the next day, I saw that I had not returned any money. I thought that it was as it should be, and so I did the right thing, that I sent just such a small amount. For those who do not know what WebMoney is all about www.webmoney.ru |
Another option is fraud - when the victim is offered a program-generator of credit card numbers, systems for hidden money debiting from other accounts / purses, etc. Often such programs are offered for money, but it is reported that 1-3 accounts can be hacked for free to get an idea of how the program works. The key point is that for the operation of such programs it is necessary to enter your card / purse number and password. At attempts of such "breaking" the entered data are transferred to malefactors that allows them to get money from the account or an electronic purse of the fan of easy profit.
The scheme in which scammers offer a card-code generator program to pay for cellular or Internet connection services is similar to the previous one, but the code generator is asked to enter the code of the card that has not yet been activated, which will serve as a kind of pattern for "breeding". As in the case of credit cards, the entered data is placed at the disposal of scammers, and the program simulates a rapid process of calculations. While the victim is waiting for the result, scammers with the help of the received data already pay their bills, using the "exemplary" user card.
"Leaky casinos"
Another kind of fraud is this: the user receives a letter with the following text: "After a long game hours, a hole in the script was found, which allows guaranteed win in an online casino. We just wonder how the admins did not notice this! .. "Next, a" winning "betting strategy is described in detail and a link to the casino site is given. Of course, not the love of humanity is driven by the authors of such messages, and no "hole in the script" actually exists. The fact that a spammer receives a certain percentage in the event of a very likely loss of a casino visitor who comes to the site through his affiliate link.
In other variants of the letters with the offer of exploitation of the vulnerability discovered in the casino, attackers offer to download (and sometimes buy) and install a program that supposedly allows using the vulnerability. In fact, such a program turns out to be a malicious spyware program.
Tempting offers of quick earnings
Such letters are characterized by the following: "This letter is NOT spam. This is really a profitable offer, from which it will be difficult to refuse. This message is sent to you only once, and if you ignore it, you will regret your whole life about the missed opportunity ... ". As a rule, further in the text of the letter it is said about the financial pyramid: the user is offered to pay the author of the letter (curator) a certain sum, and then send this letter further, having received the same amount from each of the addressees (to become their curator) plus some part of the profit from Their "wards" of a lower level. Such a scheme promises fabulous incomes to each of the participants, but in reality people who have fallen for the bait of swindlers, forever part with their money.
A somewhat more cunning way was invented by the creators of counterfeit jobs. Usually in such letters, spammers on behalf of employers promise high income to future employees and argue that nothing special needs to be done to receive them. After establishing contact with a potential victim, scammers are often not even interested in confirming the qualification of the future employee, but they ask him to send a certain amount of money for detailed information or for postage, and they are urged to hurry, since someone else can take a vacant place.
Sometimes scammers conduct targeted attacks, sending out "profitable offers" to the addresses of users who posted their data on job search sites. Applicants are invited to take part in a real international project related to the extraction of gold or diamonds, the manufacture of medical equipment, vaccines, chemicals; With investments, construction and / or contracting for services. As a rule, this business has to do with the area of employment of the applicant or his business contacts and requires from him the availability of professionalism and experience. But then the stage of payment for "administrative expenses" invariably comes, and the victim's money settles in the pocket of the scammers.
Subject: Prospective Employee
|
Attn: Prospective Employee, Spiralnergy Exploration, UK is an oil and gas exploration and production company based in the United Kingdom. The Company's driving properties and Exploration activities are focused on the UK Central North Sea. The goal of Spiralnergy Exploration in the near term is to achieve oil production from its interests in the North Sea while carrying out an active exploration / development program on both its own properties and in various joint ventures. Spiralnergy Exploration, UK hereby inform, that you have been shortlisted as one of the staff / expatriate for our upcoming project schedule commence March, 2008. The project involves the construction of a new LPG (Liquefied Petroleum Gas) Plant and Oil Wells at UK Central North Sea, UK. You are hereby require to send your detailed resume and application via fax or email. All resumes / application should be in MS Word format. Thanks for your interest. William Peters This email and any attachments to it contain information that is confidential and may be privileged. It is for the exclusive use of the intended recipient (s). If you are not the intended recipient (s) please note that any form of distribution, copying or use of this communication or the information contained in it is strictly prohibited and may be unlawful. If you have received this email in error, please return it to the sender (Spiralnergy Exploration) and delete the email from your records. |
Blackmail
To draw money spammers resort not only to the carrot, but also to the whip, namely to threats. Most often these threats are quite "innocent": we will stop sending spam only if you pay. But there are also much less innocuous, for example letters on behalf of the hired killer, demanding the recipient of a ransom in exchange for life.
Subject: BE WARN !!!
HELLO |
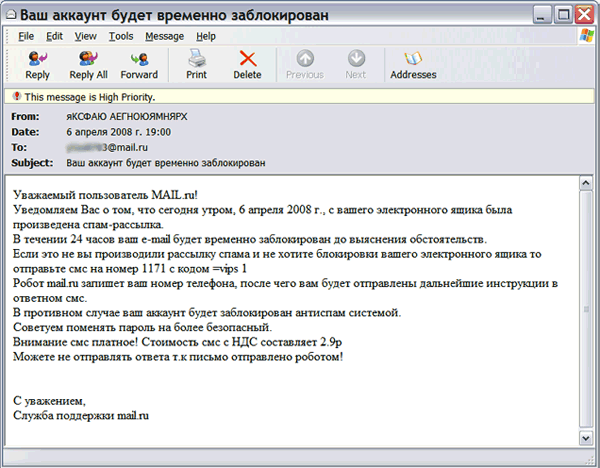
SMS to short numbers
In parallel with the use of fraudulent schemes, characteristic of the western Internet segment, Runet crooks are devising new ways of luring money. In particular, they rent short numbers from mobile operators and send out spam, the task of which is to provoke the sending of SMS messages to the rented number. The scheme of fraud is based on the fact that when sending SMS to a short number, a certain amount of money is automatically withdrawn from the sender's account, part of which is received by the lessee of the number. To achieve their goals, scammers use various tricks: from offers of free Internet access and promises of winning to threats to block the mailbox if the user does not send SMS.
|
In one such mailing, recipients were even asked to unsubscribe from spam. The spammer claimed that he wanted to "be a law-abiding citizen," and, referring to the law "On Advertising", which came into force on July 1, 2007, offered wishing to exclude his address from spam databases by sending a free SMS-message. The spammer promised that after sending the SMS the user will receive a link to the web page where the spam databases of addresses are supposedly published, and be able to remove their email from them. Needless to say, not compliance with the law was the main goal of the author of letters!
In more complex combinations, the letter can only contain a link to a specially created spammer site. On the site the user (already involved, for example, in the process of obtaining "winnings") is invited to send an SMS message to a short number. This lengthening and complication of the scheme, leading to spammers sent SMS, is designed to lull the attention of even the most vigilant users.
Conclusion
According to Kaspersky Lab's classification, fraudulent spam emails are related to "Computer fraud", which accounted for 7% of all spam in 2007. In the first quarter of 2008, this indicator decreased more than twice and amounted to 2.5%.
Although the proportion of fraudulent emails in spam has decreased, observations show that spamming becomes more dangerous: attackers sharpen their skills and increasingly conduct targeted attacks. And if in order not to fall for the bait of "well-wishers", offering easy and quick ways to enrich themselves, e-mail users have enough common sense, then more sophisticated fraud options are much harder to recognize. As for phishing, in the fight against this type of fraud, software protection can not be avoided.
We can advise users not to believe the good intentions of spammers and use software that provides reliable protection against spam, phishing and malicious programs. Despite the apparent triviality of these recommendations, their implementation will allow you to keep not only the data on your computers safe, but also money.





Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.