Utilities for surveillance, Computer espionage
Have you ever felt anxious about the security of confidential data on your computer? Do not rush to answer that you do not have confidential information. If you believe that you have "nothing to steal", you are most likely mistaken. If you at least once made a purchase in an online store, paying with a credit card or electronic money, then your computer is already a bait for a potential thief.The problem exists, and an ideal solution for it has not yet been invented. Of course, there are various ways to protect sensitive data, for example, restriction of access rights in the system, anti-virus software, firewalls, etc. Many of them we repeatedly told on pages 3dnews. However, it would be somewhat presumptuous to rely entirely on the antivirus and password protection system. In addition to the danger of a virus attack, there is a threat of a completely different kind, conditioned by the human factor. What happens when you are away from work? Perhaps, while you finish your cup of coffee in the buffet, during lunch break at work, someone reads your correspondence by e-mail?

Having acquired a foreign computer even for a few minutes, an experienced user can easily find out all the information he is interested in - the history of negotiations on ICQ and e-mail, the list of passwords used in the system, the resources links that the user viewed, not to mention the access to documents On the disk.
About utilities that help spy, and will be discussed in this review. Such programs can be used both at work to monitor the working time of employees, and at home as a means of parental control or as a tool for obtaining information about the personal life of your half.
Note that due to the specifics of the work of spyware, often antiviruses and firewalls are very suspicious of them, often taking them for malicious programs. Developers of some utilities even place an appropriate notification on their sites. However, in most cases it's enough to configure the firewall once, and it will not react to the spy anymore.
Power Spy 2009
Developer: eMatrixSoft
Distribution size: 5 MB
Distribution: shareware
The program Power Spy can be called a universal spy. It is suitable for monitoring employees' workplaces, and for monitoring the child's activity at the computer, and in order to find out what the wife does on the home PC in your absence.
The program can record all keystrokes, save screenshots of user-opened windows, record the addresses of visited websites, intercept messages sent by e-mail, and through instant messaging systems (MSN Messenger, Windows Live Messenger, ICQ, AOL Messenger, AIM, Yahoo ! Messenger, Windows Messenger and text chat Skype). In addition, it is possible to save all user-opened windows, applications being launched, typed passwords and information that is written to the clipboard.
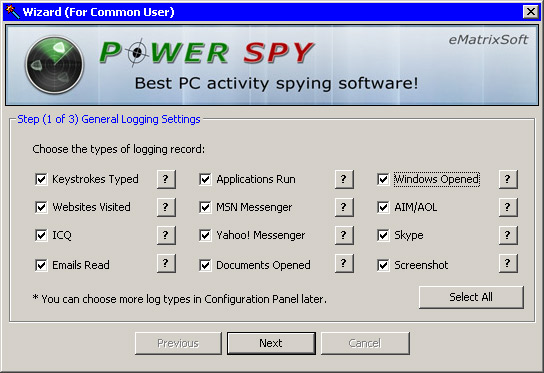
In hidden mode, Power Spy is completely invisible to the user, it does not appear in the list of running applications, does not show the icon in the system tray, it is not in the list of installed programs and in the Start menu, and in addition, the folder into which Power Spy was installed , Is also hidden. To interrupt the operation of the program or uninstall it is necessary to enter a password, and you can delete the program using its window. The administrator can call the program window with the collected data by pressing a certain key combination. Information about the activity at the computer is presented in a convenient way: screenshots can be viewed in the slideshow mode, information about the keystrokes are organized in chronological order by applications and windows, the Email tab presents the text of all the letters that the user read and sent. In addition, the program saves the contents of all documents that users have worked with. And, if the file was opened several times, then Power Spy will save it only once, which allows you to reduce the size of the report.
In addition, you can configure Power Spy to send reports by e-mail in HTML format or to upload them to an FTP server.
Real Spy Monitor 2.89
Developer: ShareStar
Distribution size: 1.4 MB
Distribution: shareware
Another utility that helps you to be aware of who, what, what and when does the computer. The program supports the work with several Windows accounts and, when creating a report, indicates which user performed certain actions. During the program setup process, you can select the accounts that will automatically start when the program is used.

Reports compiled by Real Spy Monitor include information about all the keys being pressed and the titles of the windows in which the set was made; About visited sites (addresses, headers, download time); About opened windows (the title, the path to the executable file of the program) and files; About running applications with the indication of start and close times. In addition, the program records messages exchanged by IM clients and can take screenshots at specified intervals.
The collected information can be viewed in the program window (it is called by a combination of keys
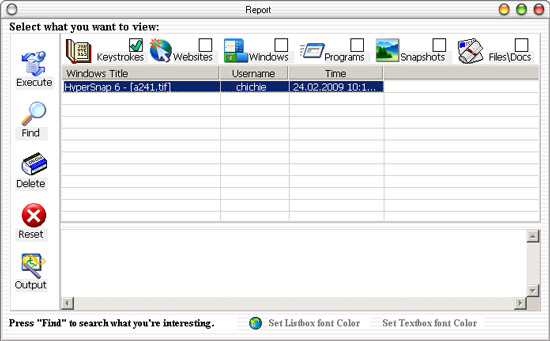
If you use a program to monitor children's actions, then evaluate the possibility of installing filters for applications and open sites. In Real Spy Monitor settings, you can specify the path to executable files that can not be started by a particular user. As for sites, you can block certain resources by entering the full address of the resource in the black list or the keyword that the program will search on the page. For young children, you can set more severe restrictions - to allow access only to those sites that appear in the "white" list.
Maxapt QuickEye 2.8.8
Developer: STBP "Maxapt"
Distribution size: 5 MB
Distribution: shareware
If some other programs of this review can equally well be used to monitor the actions of employees of the company, and to track users on the home PC, then Maxapt QuickEye is aimed primarily at corporate users. The main focus in it is on the tools for viewing and analyzing reports. Thanks to this, the chief can quickly find out how much time each employee actively worked at the computer, and which programs he ran. Interestingly, Maxapt QuickEye not only fixes open applications, but also takes into account whether active work with them was conducted. Thus, if the application window was open all day, but the user only worked with it for half an hour, Maxapt QuickEye will display it in the report.
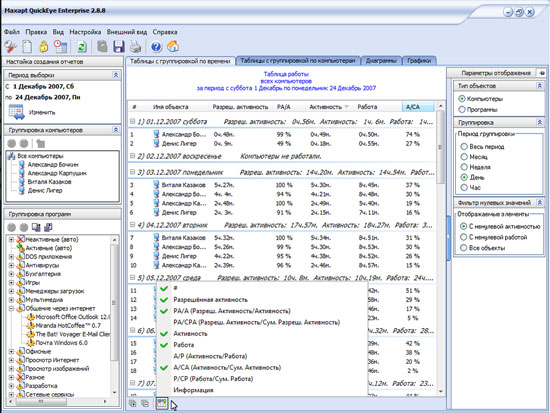
In the Maxapt QuickEye window, the applications that users work with are grouped by category. Thus, by going to the "Games" or "Communication through the Internet" category, you can see on which computer and for how long such programs were active. All data can be presented in the form of a table with grouping by computers or by time. In addition, you can see the report in the form of a chart or graph.
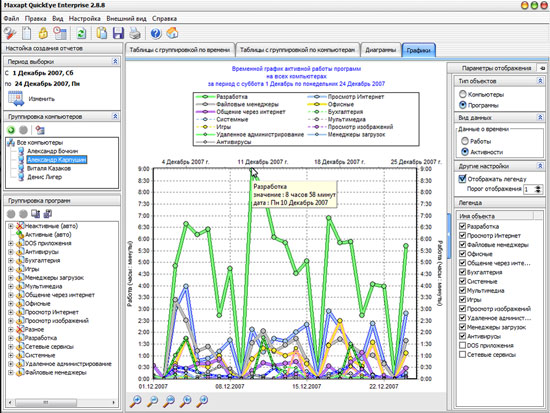
The reports provided by Maxapt QuickEye contain information about the presence of employees in the workplace. The program fixes the moments of entering the operating system, turning off the computer, putting it into sleep mode, and then automatically calculating how many hours and minutes the employee spent at the computer. In this case, from the total time when the computer was turned on, the time when it was in sleep mode is subtracted.
Using Maxapt QuickEye, you can not only receive reports on what employees spend working time, but also restrict the use of certain applications. With the help of the utility it is possible to compile a list of allowed and forbidden programs for each employee, to establish a schedule of working hours.
Mipko Employee Monitor 5.0.4
Developer: OOO Mipko
Distribution size: 4.8 MB
Distribution: shareware
Previously, the Mipko Employee Monitor program was called KGB Keylogger. The main advantage of this utility over various keyloggers is that tracking activity can be done remotely. Even during the installation process, the installation program warns about the presence of the antivirus in the system and the need to perform its corresponding configuration by adding Mipko Employee Monitor to the list of trusted applications or exceptions.
The program is very flexible implemented work with several users, in this sense Mipko Employee Monitor - an indispensable tool for the system administrator. For each user whose computers need to monitor, you can set different monitoring options. For example, for one user you can set tracking only for typed text, for another - to track only visited websites, for the third - to keep statistics of running programs, etc.
The program can work using the alarm mode. This means that when the user types certain words, the Mipko Employee Monitor marks the activity of the user with an alarm icon, and, with the corresponding settings of the program, sends a warning message to the administrator by e-mail or uploads to the FTP server.
The program is perfectly masked, its monitor can not be found either in the list of running processes or in the list of services. To display or hide Mipko Employee Monitor, you must type runmipko at the Windows command prompt or use a keyboard shortcut
Mipko Employee Monitor allows you to use tracking filters. So, it is possible to make a list of programs whose activity should be monitored, and tracking of other applications that are launched will not be performed. The log size for each of the users that are tracked can be strictly limited. By default, the program stores records about user activity up to 90 days, if necessary, this time can be increased or decreased.
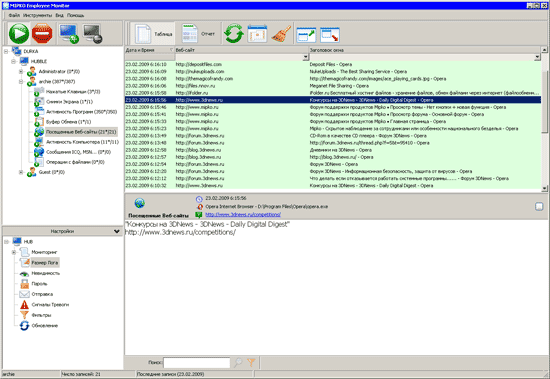
Information about the activity of the user, which this program collects, would be incomplete if there was no possibility of creating screenshots of the screen. A snapshot can be taken only for the active window or the entire working area of the screen. By the way, on configurations with multiple monitors also you can make screenshots. When you capture the entire working area, the image is obtained in the form of two combined screenshots - the first and second monitors. Screen capture is performed either at certain intervals or when a new window is opened. In the absence of any activity, the creation of screenshots automatically stops, so as not to generate the same and useless images.
Mipko Employee Monitor intercepts messages in all popular instant messaging programs - ICQ, Yahoo! Messenger, AIM, Windows Live Messenger, Miranda IM, Skype, Google Talk, Mail.Ru Agent, Qip.
Actual Spy 3.0
Developer: Keylogger Actual Spy Software
Distribution size: 1.6 Mb
Distribution: shareware
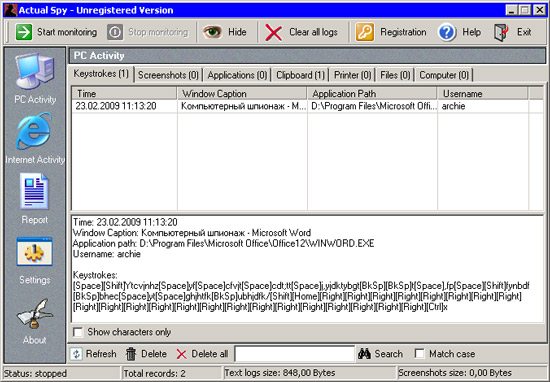
With this program you can get information about different types of active use of the computer. So, it watches the contents of the clipboard, saves information about the time of starting and closing applications, takes screenshots of the desktop at regular intervals, keeps track of the on / off time and reboot the computer. Actual Spy monitors the keystrokes and visited sites, and also monitors the documents sent to print. The program saves changes in files and directories, records any links used by the browser.
The program is hidden using a keyboard shortcut
The user activity report can be saved in text or HTML format, on one or more pages. When viewing the report generated by Actual Spy, one immediately catches the eye of the lack of the program - it only accepts keystrokes in the English keyboard layout. Therefore, if it is necessary to read, say, the text of the e-mail in Russian, reading will turn into solving the puzzle. However, the Russian text copied to the clipboard is displayed correctly.
We draw your attention to the fact that the demo version of the program can perform its functions within forty minutes. Sometimes this is enough to protect your working computer during a lunch break.
NeoSpy 3.0
Developer: MC-Soft Software
Distribution size: 2.7 MB
Distribution: shareware
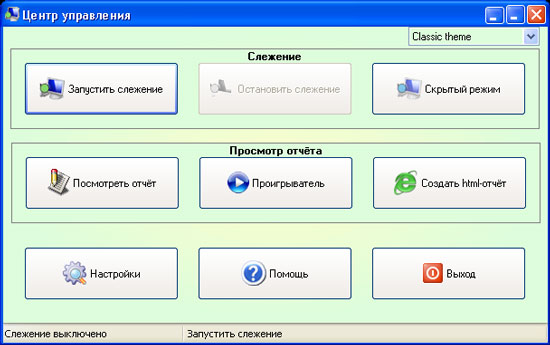
For the spy program, the most important thing is not to betray yourself. The NeoSpy developers made sure that after installation the program was invisible on the computer. Installing the utility, you can choose an administrator or hidden installation. In the latter case, shortcuts will not be created in the "Start" menu and on the desktop, the folder with the program will be hidden, it will not be visible in the list of installed applications. To start NeoSpy, the administrator will need to use the command "Start> Run".
NeoSpy can intercept messages sent by various IM clients. It is gratifying that not only popular clients among English-speaking users are supported, but also those that are installed by the majority of Russians. We are talking about Qip, Miranda and Mail.ru Agent. In addition, NeoSpy copes with interception of messages sent with & RQ, ICQ, SIM and other programs.
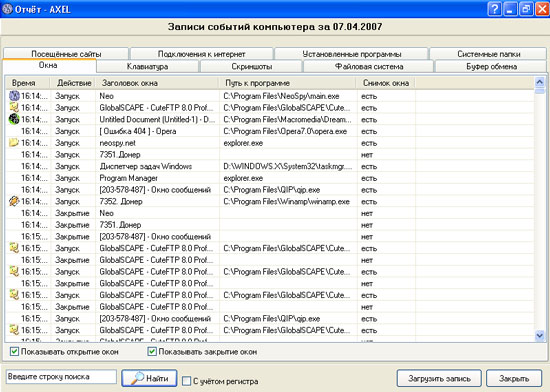
With NeoSpy, you can collect information about all the applications that run on your computer. The program saves start and run time, the path to the executable file, the window title. In addition, the report will indicate whether a screenshot was made for each of the programs. Screenshots can be viewed in the built-in utility, provided with convenient navigation tools. The module for viewing screenshots has a special timeline, so if you want to find out what the user was doing at the computer at a certain time, just move the slider on this scale to the desired position.
Using NeoSpy, you can monitor the Internet activity on your computer. The program not only stores the addresses of visited sites, but also records when the connection to the Internet was made and disconnected from it (of course, if the connection is not permanent), monitors the amount of incoming and outgoing Internet traffic.
By and large, NeoSpy makes it possible to follow all the actions that were performed on the computer. So, the program saves everything that was typed on the keyboard, stores data that was written to the clipboard, tracks changes in files, creates new files and deletes them. In addition, if necessary, you can save a complete list of applications installed on your computer.
Modem Spy 4.0
Developer: SoftCab
Distribution size: 380 kb
Distribution: shareware
This program offers a completely different way of "espionage" - a telephone. If a modem is connected to the computer, then using a small utility Modem Spy, you can record all telephone conversations. A very convenient feature, especially if the desk phone does not have this capability. Recording of telephone conversations can be performed in automatic mode, while the program will keep statistics of telephone conversations in a special call log. During recording, the sound of the interlocutor will not sound too quiet, since the program uses automatic gain control.
Audio recordings can be saved in any audio formats - MP3, WAV, etc. Recorded telephone conversations can be played through a sound card or played directly on the phone line. Modem Spy can record conversations, even with the use of modem models that support the transfer of data (data modem) only. To do this, you must connect the modem and the line input of the sound card using a special adapter. You can also use super-spy mode (Super Spy), in which the recording of calls will be carried out imperceptibly for the user.
Another possibility of the program is recording from the microphone in the voice recorder mode. Directly from the program Modem Spy it is possible to send the made records by e-mail. If the technical characteristics of the modem allow, the program can determine the number of the caller. You can record conversations without the knowledge of the remote subscriber, or with his prior notification, by including the appropriate program setting. Modem Spy has many parameters that allow you to fine-tune the modem to work with the telephone line - correctly detect the busy signal, determine the silence in the conversation and cut it out to get a file with a smaller size, include the record after a certain call, etc.
WillingWebcam 4.7
Developer: Willing Software
Distribution size: 4.6 MB
Distribution: shareware
If we are talking about telephone espionage, we can not fail to mention video surveillance. It can be implemented using a web camera connected to a computer. This simple device, which many are accustomed to use to communicate with friends, may well be a real spy.
You can turn a webcam into a spy device, for example, using the WillingWebcam program. Using it, you can remotely monitor what happens next to the computer next to which the webcam is installed. WillingWebcam can take pictures continuously at regular intervals or only when motion is detected in the frame. The received photos can be sent by e-mail or uploaded to an FTP server. In addition, WillingWebcam can notify the user about the appearance of new pictures and in other ways: by sending an SMS, launching another application, having lost the audio file.
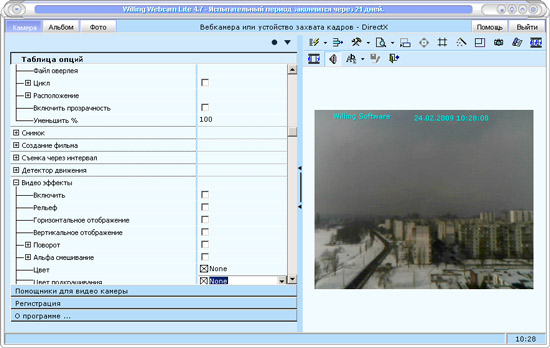
The video recorded with the program and the taken pictures can be accompanied by text captions, as well as the recording time. In addition, many effects are available, with which you can improve the quality of the image, for example, improve the clarity.
In WillingWebcam there is a built-in module for viewing images and video files, organized by the type of Explorer. In it you can view thumbnails of images, play the saved video, choose different modes of viewing the file list. If desired, the images can be viewed in full screen mode.
WillingWebcam can work in stealth mode. In this case, it will not be visible either on the taskbar or in the system tray. To exit the program from this mode, a key combination is used by default
Elite Keylogger 4.1
Developer: WideStep Security Software
Distribution size: 5,3 Mb
Distribution: shareware
WideStep Security Software releases three versions of its keyloggers - Family Quick Keylogger, Perfect Handy Keylogger and Elite Keylogger. The latter option is the most functional and has the most features.
For example, the version of Elite is absolutely not determined by antiviruses, while Perfect Handy Keylogger is defined, but not all anti-virus packages, and the Family Quick Keylogger is detected by any antivirus program. Due to the fact that the keylogger works at a low level of the kernel of the system, Windows does not slow down and provides a good "compatibility" with antivirus programs. And still, the first time Elite Keylogger was launched, the Kaspersky Internet Security 2009 package was suspicious of the new object and recommended that it be sent to quarantine.
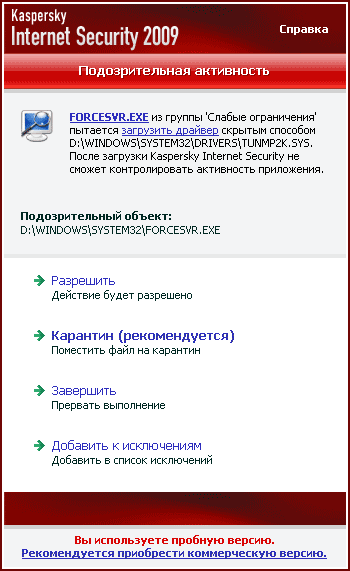
The appearance of Elite Keylogger says that it is designed not just for tracking the user, but for continuous monitoring of activity for a long time. You can view activity statistics in the program by day, using the calendar built into the program. Elite Keylogger allows you to determine the list of Windows users, which should, or, conversely, should not be tracked.
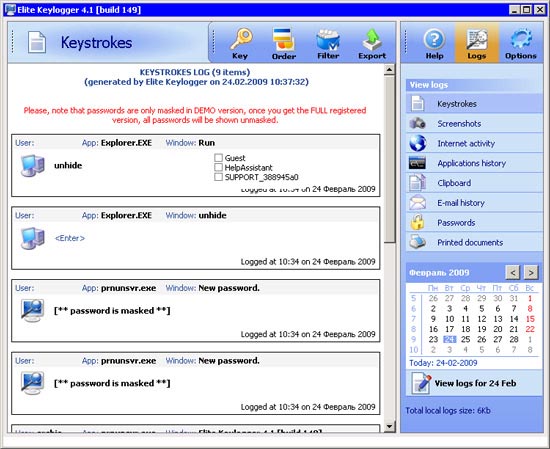
Elite Keylogger controls the operation of Internet pagers ICQ, MSN, AIM, AOL and Yahoo, monitors e-mail, application activity and printed documents. The result of the monitoring program can be sent by e-mail, uploaded to an FTP server or copied to the specified folder on a network drive.
In the program, you can set the time period after which all logs of user activity will be automatically deleted. You can also set the maximum size of the activity report, and specify the amount of the log file that will be sent by e-mail when it reaches.
We draw your attention to one detail - if you want to remove this keylogger, then neither with the standard Add or remove programs, nor even with the help of special utilities controlling Windows startup, this can not be done. In order to uninstall Elite Keylogger, you need to go to the Options section and use the Uninstall keylogger button in the interface of the utility itself.
Conclusion
Those who want to try the utility for monitoring the activity of users may notice that the choice here is quite large. The demand for such software is consistently high. First of all, such applications are claimed by organizations and firms where strict discipline reigns, and employees are subject to strict requirements as to what they do in their workplaces.
If more recently the term "keylogger" meant a utility that recorded keystrokes, today such applications allow you to control almost any kind of activity - mouse clicks, program startup, changes to system settings, etc. Moreover, using the programs described in this article , You can control the monitoring remotely, tracking in real time what the user is doing, which window is active, what text he is dialing and even with whom he is talking on the phone.
For those who are concerned about privacy, you can advise using complex protection (for example, an antivirus package and an activity monitoring utility) and rely mainly on yourself. Because for each castle the thief, unfortunately, has a master key.




Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.