Free Activation of the page VKontakte
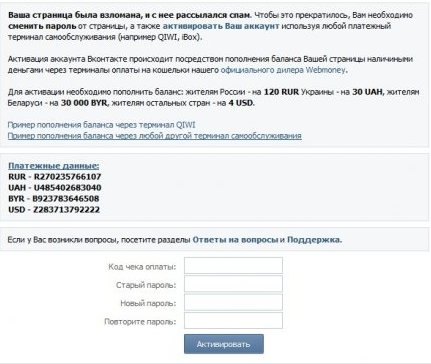
This question is asked daily by thousands of users on all sorts of forums. In most cases, a window appears on the user's computer where it is offered to send an SMS message, after sending, which is promised restoration of access to the favorite site. Another scenario is also possible. Access to your favorite sites is blocked without any warnings and extortions of money. What to do in this case? How to get yourself access to your favorite site? Today we will briefly consider one of the solutions to this problem.
First of all, I want to inform the users of the following news. Developers and owners of the resource "vkontakte.ru" do not plan to collect money for access to their site. Therefore, any message on your monitor screen, that all questionnaires will be deleted, and access to the social network is prohibited - an attempt to mislead you, extort money.
Measures to counter intruders
If a message appears on the screen of your monitor that you want to send an SMS in order to get the access code to the Vkontakte website, keep in mind - the Trojan has settled on the computer, which carefully collects information about which sites you visit, what passwords you enter. Moreover, much of this information has already been collected.
The first task is to disable the Trojan. The initial stage of the work, I would put in two simple points:
- 1.Disconnecting suspicious processes in computer memory
- 2. Remove suspicious programs from startup
If you successfully managed to solve the two points I have mentioned, you should take care of installing the antivirus program. What should I do if my antivirus software is already installed on your computer? Feel free to remove it and reinstall it.
Which antivirus is better? The best antivirus in this situation will be one that was not installed earlier. I use two free antivirus CureIt (does not require uduvovki) and AVZ4 (does not require ustunovki). Each antivirus has its drawbacks and its advantages. Which one is best suited for you.
How to find the virus? Hosts file
After all the above events are carried out, you need to start the most important thing - editing the hosts file . More information about this file can be found here .
Our first priority is to find the hosts file on your computer.
If your Windows operating system is installed on the C drive, the path to the file will be as follows: C:\WINDOWS\system32\drivers\etc
This folder should contain the hosts file .
The file does not have an extension. To edit it, right-click on the file, select "Open" and then a new window will be offered a list of programs, an example below ...
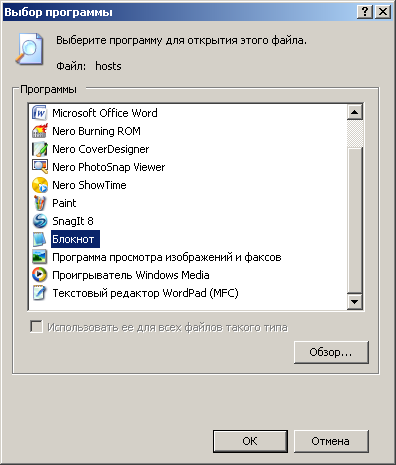
Here we are looking for the Notepad program or your favorite file editor. Select it with the mouse and click the "OK" button.
Before, to show how the wrong hosts file should look, I want you to know the contents of the original file: # Copyright (c) 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host# Copyright (c) 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
It is with this text that the file is full after installing the Windows operating system.
Now we look at our current file using the Notepad program. On an infected computer, it may well look like this, the example below ...
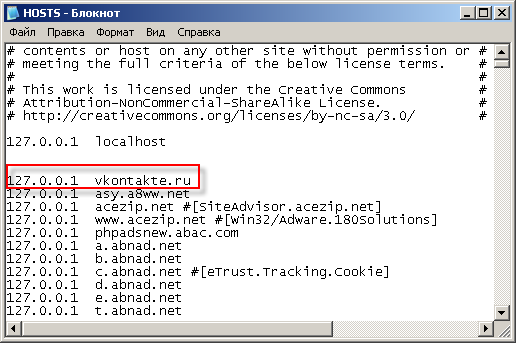
Note that 127.0.0.1 is followed by the domain names of the sites.
In fact, each line like: "127.0.0.1 vkontakte.ru" blocks access to a certain site.
In this case it is a social network "Vkontakte.ru".
Now our task is to select all the contents of the hosts file and delete all the text that was opened to our eyes.
Next, copy the original contents of hosts from our site. I suggested it to your attention for your reference above.
And we paste it into the place of just deleted data. Here's what we should get, an example below ...
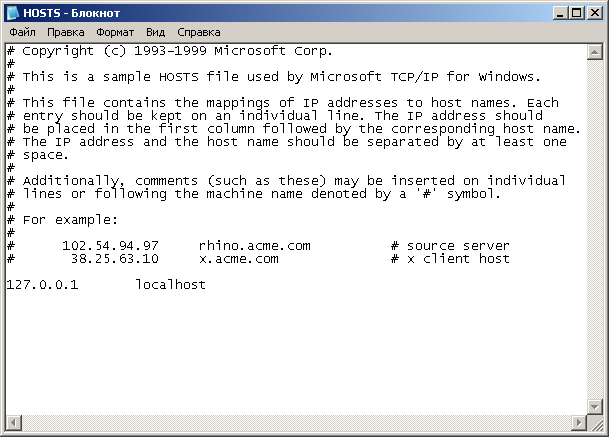
We close the Notepad. When asked to save the file, we answer "Yes".
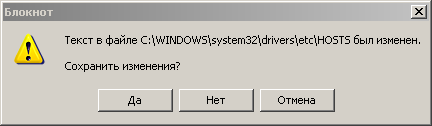
We reboot the computer. Also we try to enter on the necessary site.
According to my observations in 30-50 percent of cases, the above actions lead to a positive result.
However, there is a more complicated version.
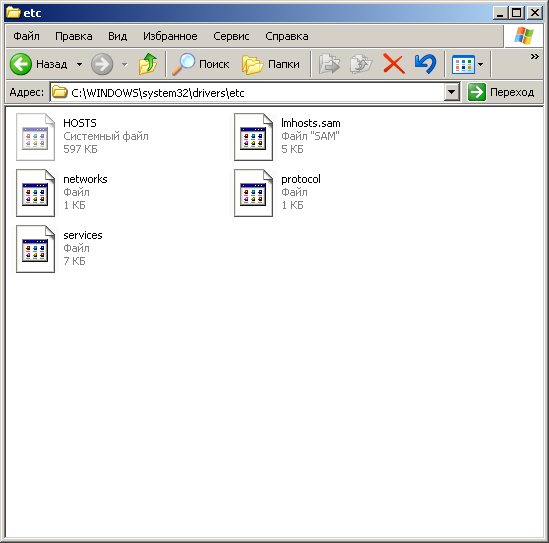
So, suppose you went to the C: \ WINDOWS \ system32 \ drivers \ etc folder and you see the following picture, the example below ...
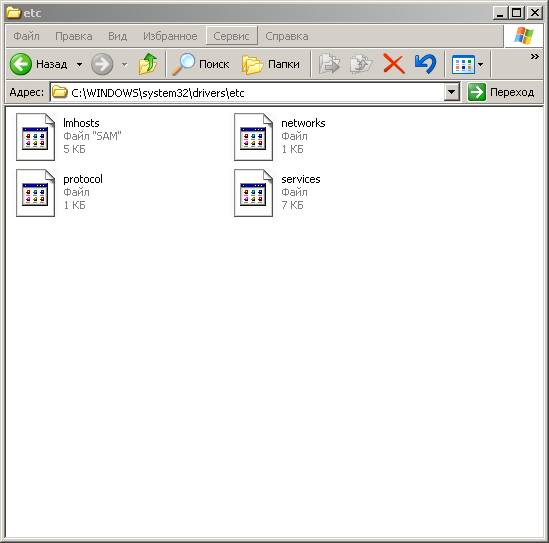
As you can see, the hosts file does not exist here!
We can see that there is a certain lmhosts file in the folder, which can be renamed to hosts.
I do not advise doing this, since this operation will not lead you to a positive result.
In this case, you need to do the following set of actions: in the main menu of Windows Explorer go to the main menu of the Service and select "Folder Options" there.
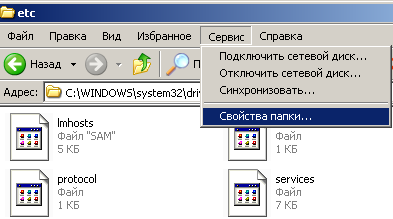
Go to the "View" tab and uncheck the box next to the following:
- - Hide protected system files
- - Hide extensions for registered file types
Now click on the radio button next to "Show hidden files and folders".
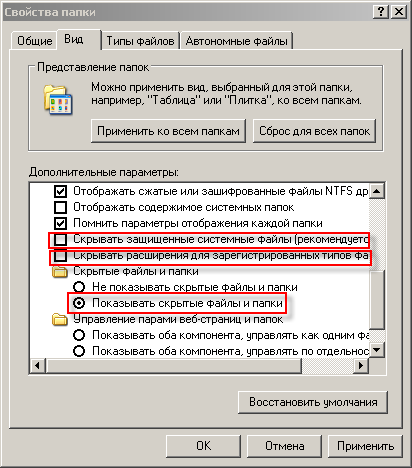
We press the "Apply" button and then the "OK" button.
The window will close, and we will see the contents of the folder C: \ WINDOWS \ system32 \ drivers \ etc that we already like.
We see that the real hosts file was hidden from our eyes. Now we see it.
However, when you try to edit and save, this window opens such a window, an example below ...
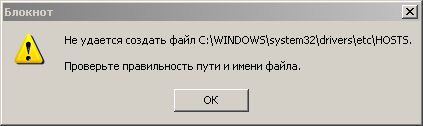
Therefore, we will proceed simpler. Delete the hosts file completely.
Select it with the mouse and click on the keyboard "Shift + Delete". Thus, our file is deleted forever, bypassing the basket.
Now create the hosts file again.
To do this, in the C: \ WINDOWS \ system32 \ drivers \ etc folder, right-click on the empty space and call the context menu.
Choose: Create - Text document, an example below ...
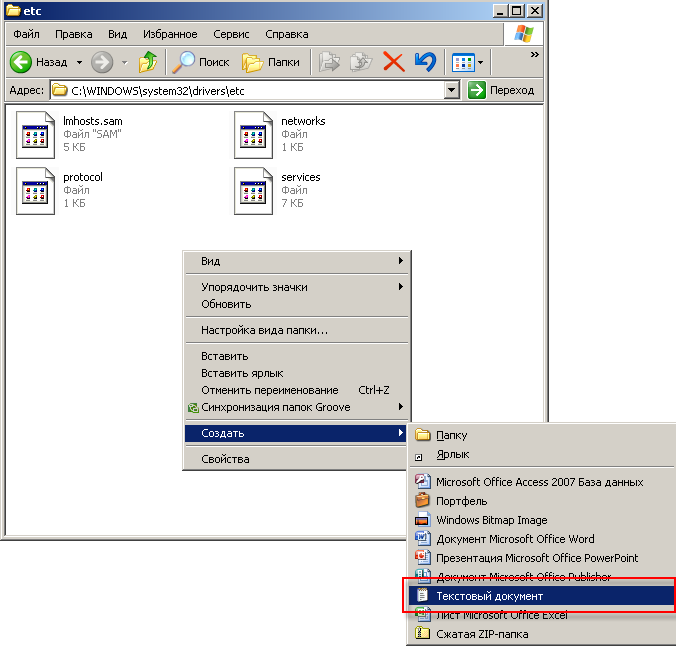
A file will appear with the name Text document.txt
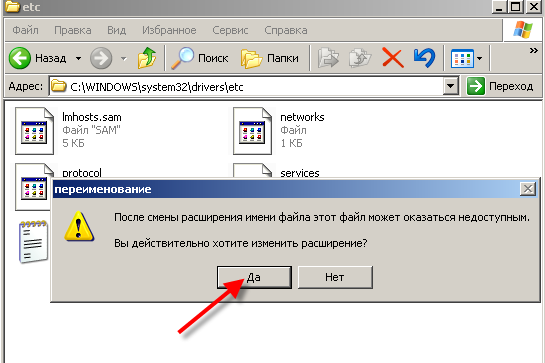
Remove the full name and extension of the file and enter it just hosts. For the request to change the extension, we answer "Yes", the example below ...
Now we paste the contents of the original hosts file, the example below ...

The file lmhosts.sam is simply deleted.
We reboot the computer. Our Vkontakte website should open.
In fairness, it should be noted that the above recipe will work not only for the social network "In contact", but also for the social network "Odnoklassniki" and other frequently visited resources of the Internet.
If this does not happen, please describe the problem in detail on our forum .
If you are a complete teapot and did not understand anything from the above, download the free Dr.Web CureIt utility, it does not require installation, it does not conflict with an already installed antivirus (you do not even have to disconnect or delete it), after a quick scan, run full. It perfectly copes with a virus that blocks some sites, including Vkontakte and Odnoklassniki!


Comments
When commenting on, remember that the content and tone of your message can hurt the feelings of real people, show respect and tolerance to your interlocutors even if you do not share their opinion, your behavior in the conditions of freedom of expression and anonymity provided by the Internet, changes Not only virtual, but also the real world. All comments are hidden from the index, spam is controlled.