Позвони мне, позвони: какие sms присылают телефонные мошенники

Фрод (англ. fraud «мошенничество») — вид мошенничества в области информационных технологий, в частности, несанкционированные действия и неправомерное пользование ресурсами и услугами.
Мошенники работают не покладая рук. Аферисты придумывают новые ловушки, чтобы выманить деньги у доверчивых граждан. Только за последнюю неделю лично получил несколько подозрительных сообщений, так или иначе связанных с транзакциями по банковским картам. Это натолкнуло на мысль рассказать о самых типичных sms, которые помогают жуликам опустошать счета. Как не попасть в сети злоумышленников и «коллекция» sms-сообщений, которуя чаще всего рассылается потенциальным жертвам.
Предлагаем вашему вниманию самые популярные виды посланий от аферистов
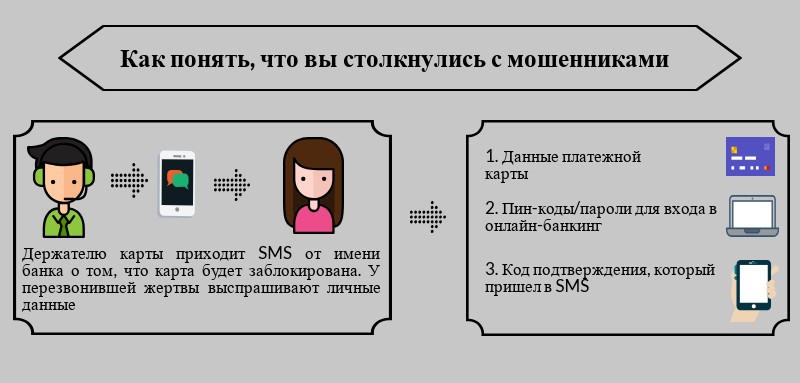
Телефонное мошенничество делят на два вида: вишинг и смишинг. В первом случае банковские реквизиты и идентификационные данные выманивают во время телефонного звонка, во втором — через sms-сообщение, которое толкает жертву позвонить злоумышленникам.
Благодаря психологическому воздействию на жертву, аферистам несложно получить желаемую конфиденциальную информацию — пин-код, CVV и номер карты.
Оказавшись в стрессовой ситуации, человек может добровольно раскрыть секретные данные. Более того, часто доверчивые жертвы сами переводят деньги на карты мошенников.
1

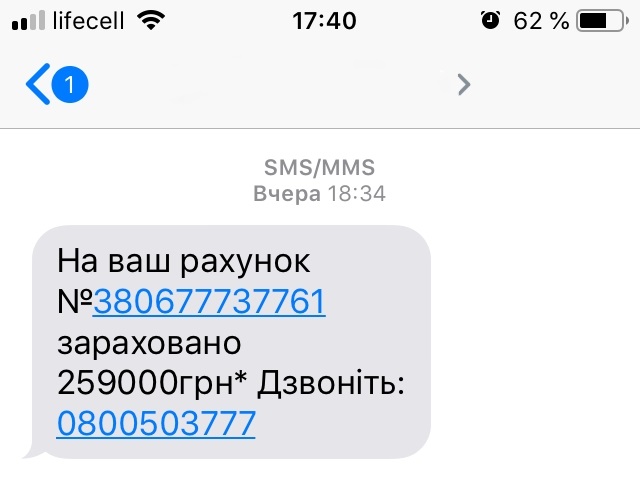
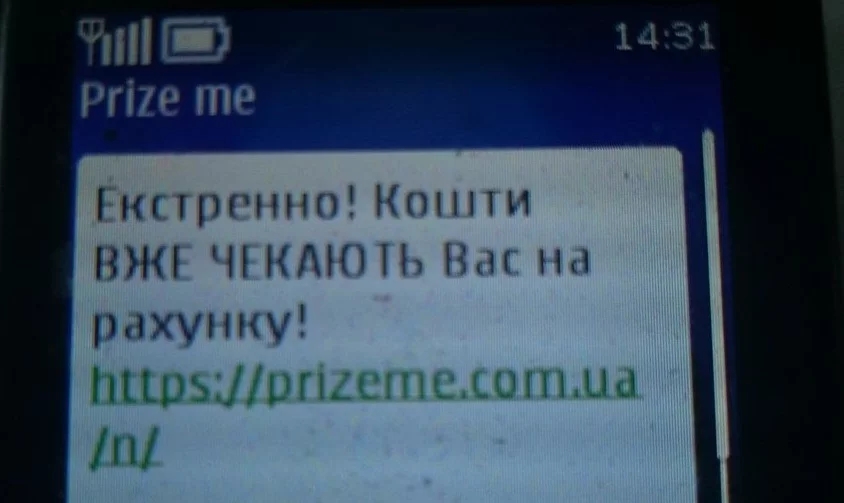
Кто не хочет получить в наследство миллион, выиграть в лотерею или стать обладателем ценного приза?
Признайтесь, вам тоже хочется, чтобы деньги внезапно свалились на голову (читай — на карту)!
Об этом прекрасно знают мошенники и заманивают украинцев новостями о счастливом выигрыше.
На ваш счет ****** зачислено 259 000 грн. Звоните: 0800503777
2

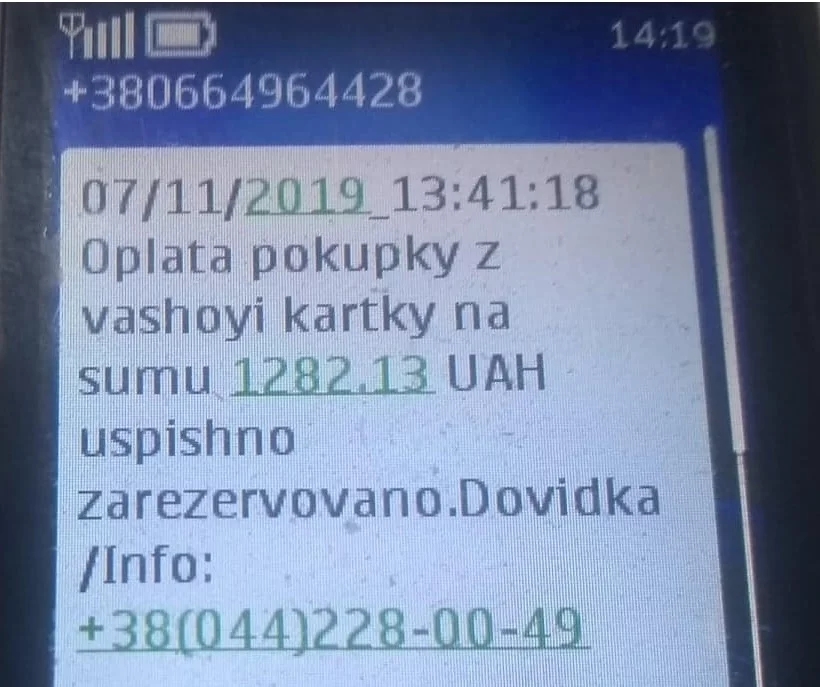
Не менее сильный эффект на жертву может оказать сообщение, что вашей картой только что кто-то оплатил дорогостоящую покупку.
Рука сама тянется, чтобы позвонить и устроить банку скандал.
Оплата покупки с вашей карты на сумму 1282.13 UAH успешно зарезервирована. Справка/Info: +38(044)2280049
3

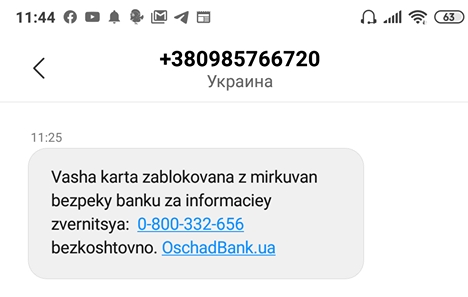
Пожалуй, даже большую панику способно вызвать сообщение о блокировании банковской карты по неизвестной причине.
Разумеется, в sms также указан телефон, по которому можно позвонить, чтоб уладить эту маленькую неприятность.
Ваша карта заблокирована из соображений безопасности банка. За информацией обратитесь: 0800332656 бесплатно. OschadBank.ua
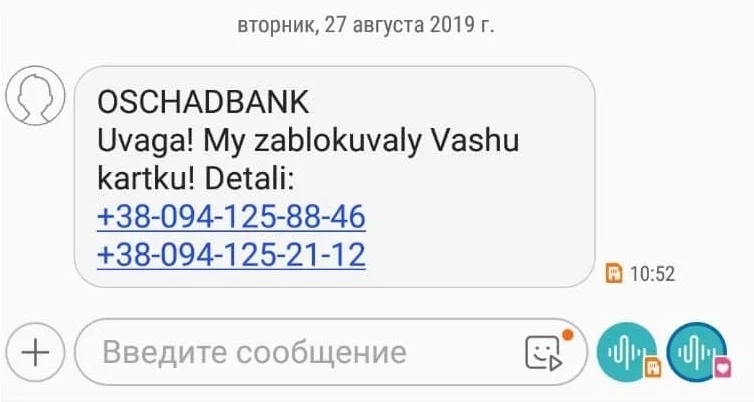
OSCHADBANK Внимание! Мы заблокировали вашу карту! Детали: +38-094-125-88-46; +38-094-125-21-12
Что происходит дальше?

В каждом случае сценарий один и тот же:
- Получатель sms набирает указанный в сообщении номер.
- Услужливый «сотрудник» банка предлагает ему назвать реквизиты карты, чтобы выяснить «недоразумение».
- После того, как жертва называет дату рождения, пин-код, CVV и номер карты, деньги со счета исчезают.
Самое неприятное: поскольку клиент сам выдал мошенникам всю информацию, банк его потери не возмещает.
По данным Украинской межбанковской ассоциации членов платежных систем ЕМА, ущерб от схем, основанных на социальной инженерии, и махинаций в интернете составил в 2018 году 245 тыс. гривен.
В первом полугодии 2019 года в базу данных было внесено 687 номеров телефонов, с которых звонили мошенники. А в межбанковский черный список попало 1 004 человека, которые получали несанкционированные переводы денег.
ЕМА создала специальный сайт с черным списком телефонных мошенников — Сhertofon. Пострадавшие оставили там уже более 300 контактов аферистов и различные варианты текстовых сообщений, которые присылают мошенники.
SMS фрод

 За 2005 год мировые сотовые операторы потеряли от сотового фрода около 25 миллиардов долларов. По данным Международной ассоциации сотовой телефонии (CTIA — Cellular Telecommunications Industry Association), ежегодные потери от «двойников» у операторов стандарта D-AMPS/AMPS во всем мире составляют около 1 млрд. USD. Международная ассоциация операторов сетей GSM выработала свою классификацию для фрод-преступлений. По данным Mummert+Partner, более 1,5 млн обладателей мобильных телефонов ежегодно отказываются оплачивать выставленные счета.
За 2005 год мировые сотовые операторы потеряли от сотового фрода около 25 миллиардов долларов. По данным Международной ассоциации сотовой телефонии (CTIA — Cellular Telecommunications Industry Association), ежегодные потери от «двойников» у операторов стандарта D-AMPS/AMPS во всем мире составляют около 1 млрд. USD. Международная ассоциация операторов сетей GSM выработала свою классификацию для фрод-преступлений. По данным Mummert+Partner, более 1,5 млн обладателей мобильных телефонов ежегодно отказываются оплачивать выставленные счета.
SMS фрод
Фрод используется для воровства средств с мобильных телефонов. Фрод — это метод превышения лимита количества отправляемых SMS-запросов, обусловленный техническими возможностями платформы ОСС, приводящий к получению абонентом заказываемых услуг без фактической их оплаты. Возможен вариант открытия платного сервиса, со способом оплаты посредством SMS-сообщений. При этом технически возможно получение отрицательного баланса на SIM-карте с дебетным тарифным планом. Для предотвращения этого вида мошенничества используется Фрод-порог, который обновляется для каждого номера 1 раз в 60 минут.
Смишинг
За счёт SMS-рассылки многие мошенники выманивают у пользователей сотовой связи деньги или важную конфиденциальную информацию. Данная область мошенничества называется смишинг (англ. SMiShing — от «SMS» и «фишинг»).
Варианты GSM-фрода
- При подписке на какой-то контент за условную плату клиенту в договор включают очень высокий тариф на отписку, а после делают всё возможное, чтобы клиент решил отписаться.
- Невозвраты по SIM-картам кредитных тарифных планов
- Оформление SIM-карт на потерянные документы с тем, чтобы полученные SIM-карты с роумингом использовать за границей. При этом счета за разговоры местный оператор отсылает оператору, выпустившему SIM-карту, с некоторой задержкой, а пока платит за разговоры самостоятельно.
- откровенный обман, когда звонящий говорит, что, переводя небольшую сумму на его телефон, вы помогаете своему родственнику, попавшему в аварию или в другую затруднительную ситуацию.
- сотовый кэш-бокс
- Stolen Phone Fraud
- Subscription Fraud
- Access Fraud
Мобильное мошенничество
 В последнее время получили довольно широкое распространение несколько схем мошенничества, связанных с услугами мобильной связи, в частности, с короткими номерами для отправки SMS. Мошенникам принадлежит большая часть рекламы в мобильном интернете (WAP), мошеннические предложения отправить SMS на короткий номер довольно часто встречаются в спам-рассылках по электронной почте, в социальных сетях, сетях обмена мгновенными сообщениями. Ответственность за мошенничество предусмотрена уголовной статьей.
В последнее время получили довольно широкое распространение несколько схем мошенничества, связанных с услугами мобильной связи, в частности, с короткими номерами для отправки SMS. Мошенникам принадлежит большая часть рекламы в мобильном интернете (WAP), мошеннические предложения отправить SMS на короткий номер довольно часто встречаются в спам-рассылках по электронной почте, в социальных сетях, сетях обмена мгновенными сообщениями. Ответственность за мошенничество предусмотрена уголовной статьей.
SMS-алармы
Термин SMS-аларм в настоящее время наиболее часто употребляется владельцами WAP-сайтов для обозначения мошеннического приложения для мобильного телефона или смартфона, отсылающего SMS-сообщения на короткие номера. Существует мнение, что SMS-аларм появился в WAP-рутине в 2005 году у известного на то время wap-мошенника с ником «джокер», который и дал данному приложению название «SMS-аларм». Существует легенда, что изначально приложение разработала компания Motorola для поиска утерянного телефона, но компании запретили реализацию данного проекта из-за его вирусной основы. Такие приложения часто распространяются под видом ICQ-клиентов, «последних» или улучшенных версий Opera Mini и других популярных java-приложений и игр — как правило, номер версий сильно завышен. Поскольку большинство мобильных телефонов выдают запрос перед отправкой Java-приложением SMS-сообщения, создатели SMS-алармов идут на различные хитрости, чтобы заставить пользователя нажать нужную клавишу в нужный момент, не успев среагировать на предупреждение на экране. Приложения для смартфонов (известны SMS-алармы для Symbian, Android) могут отправлять SMS без каких-либо предупреждений, а также автоматически загружаться в фоновом режиме, в результате чего списание денег происходит без видимой для абонента причины.
Мошенничества с премиум-сайтами
У многих мобильных операторов доступ к отдельным wap-ресурсам с платным контентом оплачивается по особому тарифу, значительно более высокому, чем обычный. Таким образом, пользователь может приобрести ту или иную мелодию, игру и т. д. без отправки смс на короткий номер, оплатив непосредственно факт её скачивания. Мошенники могут выкладывать прямые ссылки на контент на премиум-ресурсах на бесплатных сайтах без специальных предупреждений, либо даже помещать на якобы бесплатные сайты изображения (часто даже из одного прозрачного пикселя), размещенные по адресам с особой тарификацией, в результате чего пользователь, ничего не подозревая, оплачивает просмотр внешне обычного сайта по более высокому тарифу. Обычно именно на такие ресурсы ведут ссылки типа «Скачать XXX бесплатно» в рекламных блоках на российских WAP-сайтах. Сайты с премиум-тарификацией также могут «посещать» различные мошеннические приложения для мобильных телефонов.
Мошенничество с подпиской на услугу
Заключается в том, что пользователя обманным путём убеждают перейти по ссылке, служащей для подписки на платные услуги. Для реализации схемы мошенникам нужен номер мобильного телефона пользователя. Часто подобные ссылки рассылаются в SMS под видом ссылок на поздравительные открытки. В новой схеме номер мобильного телефона получают от оператора без запроса пользователя, остаётся в лучшем случае только согласиться на услугу ― у мошенников номер телефона уже есть. Например, при использовании мобильного интернета, оператор передаёт номер мобильного телефона сайту dfiles.com; номер телефона трансформируется в wap.anyOperator.com. Если развить данный способ раскрытия информации о пользователе третьим лицам, то с помощью AJAX или вредоносной программы на компьютере и/или телефоне пользователя возможно «выдернуть» номер телефона пользователя и затем как минимум манипулировать подписками пользователя, а дальше уже включается фантазия.
«Срочно требуется донор редкой третьей отрицательной группы крови»
В социальные и IM-сети запускается сообщение о том, что «ребенку нужна редкая третья отрицательная группа крови», телефон «для связи» и просьба переслать всему списку контактов. Указанный номер телефона — платный, после установления соединения автоответчик воспроизводит гудки, что заставляет многих людей перезванивать несколько раз.
SMS с просьбой перевести деньги
Рассылаются сообщения с просьбой перевести деньги на тот или иной мобильный номер (например, «Мама, срочно положи 100 рублей на номер +380*********, когда приеду, верну»). Текст сообщения подбирается таким образом, чтобы какая-либо значительная часть получателей могла принять такое SMS за отправленное кем-то из близких людей. Также мошенники могут тем или иным способом убедить жертву (например, представившись сотрудником оператора сотовой связи) отправить USSD-запрос, предназначенный для перевода денег с его счета на их номер.
Получила распространенность и другая схема: сначала мошенник посылает SMS о том, что владельцу мобильного телефона перечислены деньги, а затем с этого же мобильного приходит просьба вернуть деньги. Мошенники давят на жалость, добавляя небылицы про больных родственников и всякие несчастья в их семье. Данный способ мошенничества легко определить, так как сообщение о перечислении денег приходит только от операторов мобильной связи, а не с частных номеров.
Ещё вариант: абоненту приходит уведомление о пополнении счёта, и он действительно пополняется. Затем приходит SMS: «Случайно перевёл вам 100 грн. Сможете вернуть?». Как только абонент переводит 100 грн., «ошибочно переведённые» 100 грн. со счёта исчезают. Операторы сотовой связи предоставляют возможность возврата ошибочно переведённых денег.
Имитация технических помех
Совсем недавно в Германии участились такие случаи мошенничества, когда злоумышленники звонят жертве, имитируя с помощью технических средств помехи. В это время незнакомый голос на другом конце линии задает вопросы вроде: «Вы меня слышите?» или «Хорошо ли вам меня слышно»? Далее полученные обманным путем ответ «Да» вырезается из записанного разговора и подставляется в качестве утвердительного ответа на вопрос, к примеру: «Хотите ли вы подписаться на данную услугу?». Далее преступники пытаются получить с псевдоклиента деньги за услуги или товар, которые он никогда не заказывал. Мошенники присылают счета и могут угрожать использованием в качестве доказательства в суде фальшивое телефонное соглашение.

Via minfin.com.ua & wiki
Created/Updated: 13.12.2019
 |
|